
Microsoft Mandates DMARC for Bulk Email by May2025
Overview
The fight against email-based threats is intensifying. Following the lead of Google and Yahoo, Microsoft has officially announced the mandatory implementation of email authentication protocols, SPF, DKIM, and DMARC, for high-volume email senders, effective May 5, 2025. Domains sending over 5,000 daily emails to Microsoft's platforms, including Outlook.com, Hotmail.com, and Live.com, will be required to authenticate their messages. Initially, non-compliant messages will be redirected to recipients' Junk folders, with eventual total rejection expected if compliance isn't achieved. This enforcement represents a critical step in securing global email communications from spoofing and phishing threats (Microsoft Tech Community).
Understanding Email Authentication
Email authentication has become essential in combating increasingly sophisticated phishing and spoofing attacks. Three core standards have been adopted widely:
- Sender Policy Framework (SPF: RFC 7208): Verifies the legitimacy of the sending mail server, ensuring messages originate from authorized infrastructure. SPF helps prevent sender address forgery by defining authorized sending sources in DNS records.

- DomainKeys Identified Mail (DKIM: RFC 6376): Cryptographically signs email messages, allowing recipients to confirm message content hasn't been altered in transit. DKIM leverages public-private key pairs to ensure message integrity and authenticity.
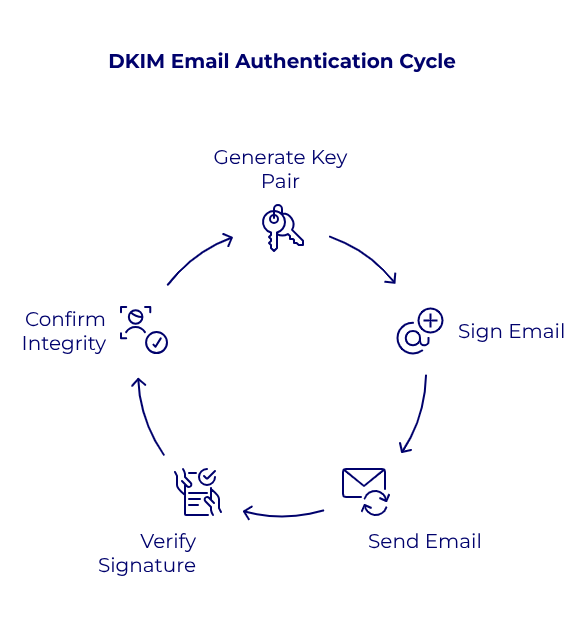
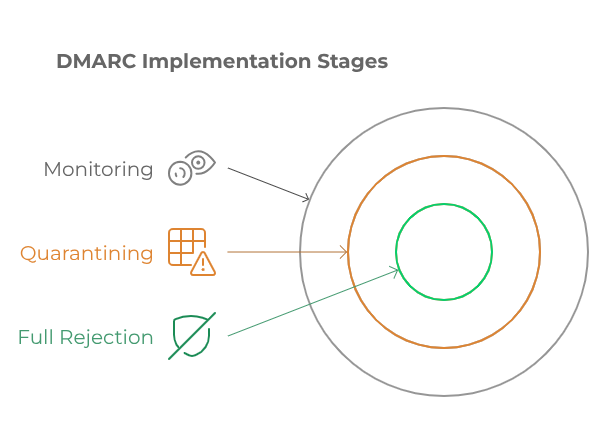
- Domain-based Message Authentication, Reporting, and Conformance (DMARC: RFC 7489): Combines SPF and DKIM to enforce domain alignment, verify authenticity, and provide reporting mechanisms for senders to track email usage and potential abuse. DMARC is recommended to be implemented in three incremental stages: initial monitoring (p=none), intermediate quarantining of suspicious messages to test the policy impact (p=quarantine), and full rejection of unauthorized emails to achieve DMARC compliance (p=reject).
Email Content and Delivery Best Practice Guidance
To help the email ecosystem thrive and ensure that legitimate communications reach users' inboxes, major providers like Google, Yahoo, and Microsoft have released a unified set of technical and content-based requirements. This section consolidates these guidelines into a single resource for senders seeking to avoid spam filtering and maintain high deliverability rates.
1. Message Headers & Structural Integrity
2. Content Hygiene and Formatting
3. Infrastructure and Technical Configuration
4. Recipient List Management
5. Engagement and Complaint Monitoring
6. Summary Recommendations
- Align headers and domains with clear, professional identities.
- Respect opt-in and unsubscribe behaviors with transparent mechanisms.
- Structure content to be clean, concise, and free of deceptive or spammy characteristics.
- Maintain technical hygiene through DNS, TLS, SPF limits, and ARC usage.
- Monitor sender reputation and user engagement continuously.
- Ensure SPF and DKIM are properly configured and aligned with the domain in the
Fromp=none.
Immediate Impact and Risks of Non - compliance
As of May 2025, domains that fail SPF or DKIM checks or lack a correctly configured DMARC policy with alignment will risk having their emails marked as spam or not delivered at all. Misalignment occurs when the domain used in the message's "From" address doesn't match the domains authenticated by SPF or DKIM.
Organizations failing to comply face significant risks, including diminished deliverability rates, compromised customer trust, and increased susceptibility to impersonation attacks. These impacts directly affect an organization's reputation, customer engagement, and potentially, its revenue.
Actionable Recommendations for Immediate Implementation
To effectively prepare for these mandatory standards, organizations should:
- Audit current DNS records: Utilize tools such as "dig" or Google DNS to verify SPF, DKIM, and DMARC records.
- Begin with Monitoring (p=none): Initially deploy DMARC in monitoring mode to understand email flows and detect anomalies without risking legitimate email delivery.
- Gradually enforce stricter policies: Move from quarantine to full rejection while monitoring.
- Ensure domain alignment: "From" domain must match what’s authenticated via SPF or DKIM.
- Maintain email hygiene: Clean lists, include a clear opt-out option, and avoid using misleading subject lines or headers.
Start Your DMARC Journey with CTM360 Free Community Edition
To support organizations navigating these changes, CTM360 offers a complimentary zero-cost Community Edition platform. It allows comprehensive monitoring, management, and enhancement of your DMARC records and email authentication setup. This proactive approach helps organizations reduce risks associated with impersonation attacks and maintain reliable email communication.
Join CTM360 Community Edition today, no hidden costs, simply real security.
Reference:
Disclaimer:
The information contained in this document is meant to provide general guidance and brief information to the intended recipient pertaining to the incident and recommended action. Therefore, this information is provided "as is" without warranties of any kind, express or implied, including accuracy, timeliness, and completeness.
Consequently, under NO condition shall CTM360®, its related partners, directors, principals, agents, or employees be liable for any direct, indirect, accidental, special, exemplary, punitive, consequential, or other damages or claims whatsoever including, but not limited to loss of data, loss in profits/business, network disruption...etc., arisina out of or in connection with this advisory.
For more information: Email: monitor@ctm360.com Tel: (973) 77 360 360

Essential Cybersecurity Habits
Overview

In today’s digital landscape, safeguarding personal and professional data is more critical than ever. Cyber threats such as phishing, credential theft, and financial fraud are increasingly sophisticated, making proactive security measures essential. This advisory highlights two fundamental steps to strengthen your online security: enabling Two-Factor Authentication (2FA) and managing browser storage of sensitive data. By implementing these practices, you can significantly reduce the risk of unauthorized access and protect your accounts from common cyber attacks.
Strengthen Account and Browser Security
Strengthening online security requires two essential measures: Activating Two-Factor Authentication (2FA) and controlling browser storage of sensitive data. 2FA provides an additional security layer beyond passwords, significantly reducing unauthorized access risks.
The following sections contain step-by-step instructions for enabling 2FA across major email platforms including Gmail, Outlook and Yahoo. Detailed guidance is also provided for disabling auto-save functionality for passwords and payment information in common browsers such as Chrome, Firefox and Edge. Implementing these security measures enhances protection against prevalent cyber threats including phishing attacks, credential theft and financial fraud.
Enable Two-Factor Authentication (2FA)
Why it matters:
2FA adds an extra layer of security, making it harder for attackers to access your accounts, even if they have your password.

Disable Password Saving in Your Browser
Why it matters:
Malware can easily extract saved passwords from browsers.

Disable Credit Card Autofill in Your Browser
Why it matters:
Saved credit card details are a prime target for malware.

Essential Security Recommendations
- Maintain a Low Profile Online: Limit personal and professional information shared publicly to minimize risks.
- Verify Communications: Always confirm unexpected emails or messages, especially those requesting sensitive information or urgent actions.
- Carefully verify email senders, Scammers often use realistic but fake emails.
- Be skeptical of emails with poor grammar, urgent requests, or unexpected attachments.
- Avoid clicking links type URLs directly into your browser.
- Regularly update your device, software, and antivirus programs.
- Frequently scan your devices using trusted antivirus and anti-malware solutions.
- Avoid downloading software from unknown or suspicious sources.
- Use a VPN on public Wi-Fi networks to encrypt your internet connection.
- Educate yourself regularly about new cyber threats and scams.
- Immediately report suspicious activity to your email or financial provider.
- Regularly review your account activity and set up alerts for unusual behavior.
- Use secure password managers/FIDO devices.
- Always manually enter credit card details only on trusted sites.
References
Disclaimer:
The information contained in this document is meant to provide general guidance and brief information to the intended recipient pertaining to the incident and recommended action. Therefore, this information is provided "as is" without warranties of any kind, express or implied, including accuracy, timeliness, and completeness. Consequently, under NO condition shall CTM360®, its related partners, directors, principals, agents, or employees be liable for any direct, indirect, accidental, special, exemplary, punitive, consequential, or other damages or claims whatsoever including, but not limited to loss of data, loss in profits/business, network disruption…etc., arising out of or in connection with this advisory.
For more information: Email: monitor@ctm360.com Tel: (+973) 77 360 360

TRAP10 Mini App Scam
Overview:
CTM360 has discovered a new variation of scam tactics using Telegram Mini Apps and social media ads in a Ponzi-style scheme. Scammers impersonate financial institutions, leveraging Meta Ads, Telegram Ads, and fake social media accounts to lure victims into fraudulent investment platforms.
These platforms, embedded within Telegram, present a polished interface that mimics legitimate trading sites. Victims are enticed with promises of high returns, referral bonuses, and exclusive investment opportunities. Once inside, they are encouraged to deposit cryptocurrency, believing they are engaging in real trading. However, withdrawals are consistently blocked when users attempt to cash out.

CTM360 Observations
Resource Development
Telegram Mini App
- A Mini App in Telegram is a lightweight web application that runs within the Telegram interface, allowing users to interact with services like payments, games, or trading platforms without leaving the app.
- Scammers embed these fake websites inside Telegram Mini Apps, making them accessible within Telegram itself.
- Users interact with the fake platform through Telegram bots keeping them within the scam ecosystem.
Scammers also create fake websites with dedicated domains that mimic real platforms, solely for fraudulent trading, deposits, and referral scams.

Trigger
Scammers lure victims with false promises of high, risk-free returns, financial incentives like bonuses and referral rewards, and fake branding to appear credible. They create urgency with limited-time offers and countdowns to pressure quick investments.
Distribution
Scammers spread the fraud across multiple platforms:
- Meta & Telegram Ads – Paid ads and channels drive users to fake trading platforms.
- Telegram Bots & Channels – Used to lure victims into scam sites and mini-apps.
- Social Media & Messaging Apps – Victims unknowingly spread the scam by inviting friends for bonuses.
By using ads, fake profiles, and victim referrals, scammers rapidly expand their reach.

Target Interaction
Impersonated and Bogus Profiles
- Fake social media accounts are created to promote, manage and provide fake customer service to the victims
- We have also noticed scammers impersonating financial institutions, investment platforms and other industry organizations on Telegram to lure victims.
Impersonated or Bogus Websites embedded within Telegram Mini App
- The scam operates within a Telegram Mini App, where victims are redirected to the fake investment website.
- The Mini App will retrieve victim’s Telegram details and allow them quick access on these fake websites without sign-up.
- Upon sign-up, victims are requested to deposit funds and trade but withdrawals are blocked.

Motive
- PII Harvesting – Scammers collects your email address, phone number, Telegram IDs during the sign up process.
Monetization
- Payments to Cryptocurrency Wallets – Victims are tricked into transferring funds via cryptocurrency (e.g., USDT, BNB, TRX) to scam-controlled wallets.
- Selling Data on the Dark Web – The stolen credentials, Telegram IDs, emails, and phone numbers can likely be sold on underground forums or leveraged for future cyber criminal activities
Recommendations
For Individuals:
- Avoid Telegram Mini Apps for Trading – Scammers use them to bypass security measures.
- Verify Websites & Domains – Always check official sources before engaging in financial transactions.
- Use 2FA on All Accounts – Protect Telegram and crypto wallets from unauthorized access.
- Never transfer funds to an account without verifying the purpose and recipient independently.
For Businesses:
- Scan social media, Telegram, and ad networks for scams related to your brand and report them accordingly.
- Work with platforms to remove and takedown fraudulent sites.
- Educate and warn users on common fraud schemes.
Disclaimer
The information contained in this document is meant to provide general guidance and brief information to the intended recipient pertaining to the incident and recommended action. Therefore, this information is provided "as is" without warranties of any kind, express or implied, including accuracy, timeliness, and completeness. Consequently, under NO condition shall CTM360®, its related partners, directors, principals, agents, or employees be liable for any direct, indirect, accidental, special, exemplary, punitive, consequential, or other damages or claims whatsoever including, but not limited to: loss of data, loss in profits/business, network disruption…etc., arising out of or in connection with this advisory.
For more information:
Email: monitor@ctm360.com Tel: (+973) 77 360 360

Securing Browsing Extensions
Summary:
In December 2024, hackers compromised at least 35 Google Chrome extensions, affecting approximately 2.6 million users. The attack exploited phishing emails sent to developers, masquerading as Google policy violation notices. These emails tricked developers into granting permissions to a malicious OAuth application named
“Privacy Policy Extension.
” Once authorized, the attackers gained control over the extensions, injecting malicious code to steal user data, particularly targeting Facebook credentials and business accounts. Browser extensions can significantly enhance productivity by adding new features to web browsers like Microsoft Edge and Google Chrome. However, they also pose significant security risks, as malicious or compromised extensions can lead to data breaches, malware infections, and unauthorized access to corporate networks. It is crucial for organizations to control, block, or manage browser extensions to minimize security risks, particularly in an enterprise environment. This advisory outlines the steps to block and protect browser extensions for Microsoft Edge and Google Chrome, and it also includes specific guidance on managing extensions using Microsoft Intune.
Risks Associated With Browser Extensions
● Data Exposure: Some extensions can access sensitive data (e.g., browsing history, credentials, and files), potentially exposing confidential information.
● Malicious Extensions: Cybercriminals can create or compromise extensions, making them a vector for malware distribution or data exfiltration.
● Phishing Risks: Extensions may manipulate web content, tricking users into providing sensitive information.
● Performance Degradation: Some poorly coded extensions can slow down browsers or degrade system performance.
Managing Browser Extensions Using Group Policy
A. Microsoft Edge
Using Group Policy (Windows)
1. Open the Group Policy Management Console (GPMC).
2. Navigate to: Computer Configuration > Administrative Templates > Microsoft Edge > Extensions
3. Set the following policies:
a. Control which extensions are installed silently: Specify allowed extensions by adding their extension IDs.
b. Configure extension management settings: T o block all extensions, set this policy to "*" (deny all).
c. Configure the list of force-installed extensions: If any extension is necessary for business, add the corresponding extension ID here.
B. Google Chrome
Using Group Policy (Windows)
1. Open the Group Policy Editor.
2. Navigate to: Computer Configuration > Administrative Templates > Google > Google Chrome > Extensions
3. Set the following policies:
a. Block external extensions: Set the policy to block all extensions unless specifically allowed by adding the extension IDs.
b. Configure extension install allow list: If certain extensions are necessary, add their extension IDs here.
c. Configure extension install blocklist: Add a wildcard"*" to block all extensions.
Managing Browser Extensions Using Microsoft Intune
Organizations using Microsoft Intune for endpoint management can apply policies to control browser extension installations across all managed devices. This approach is particularly useful for managing large numbers of endpoints efficiently.
Blocking Extensions in Microsoft Edge Using Intune
1. Sign in to Microsoft Endpoint Manager Admin Center.
2. Navigate to: Devices > Configuration profiles > Create profile
3. Choose:
a. Platform: Windows 10 and later.
b. Profile type: Settings catalog.
4. In the Configuration settings, search for Extensions under Microsoft Edge:
a. Allow specific extensions to be installed (User): Specify allowed extension IDs
b. Control which extensions cannot be installed (User): Add a wildcard"*" to block all extensions.
5. Assign this profile to your target groups (specific users or devices).
Blocking Extensions in Google Chrome Using Intune
1. Sign in to Microsoft Endpoint Manager Admin Center.
2. Navigate to: Devices > Configuration profiles > Create profile
3. Choose:
a. Platform: Windows 10 and later.
b. Profile type: Settings catalog.
4. In the Configuration settings, search for Extensions under Google Chrome\Extensions:
a. Configure extension installation allow list (User): Specify allowed extension IDs
b. Configure extension installation blocklist: Add a wildcard"*" to block all extensions.
5. Assign this profile to your target groups (specific users or devices).
Note: These steps are mentioned for user-based controls. Similar configuration steps can be applied for device-based controls.
Best Practices for Managing Browser Extensions
● Audit Extensions Regularly: Regularly audit the extensions installed on users’ browsers to detect unauthorized or risky extensions.
● User Training: Educate users about the risks associated with browser extensions and how to identify malicious ones.
● Implement a Zero-Trust Model: Always assume that extensions can potentially be compromised. Apply the principle of least privilege when granting extension permissions.
● Use Security Solutions: Consider deploying security solutions that can monitor and block malicious browser activities, including suspicious extension behavior.
Conclusion
Controlling browser extensions in Microsoft Edge and Google Chrome is a critical aspect of securing enterprise endpoints. By implementing the steps outlined above, organizations can significantly reduce the risks associated with browser extensions. Whether you manage your endpoints using Group Policy or Microsoft Intune, these controls can help protect your network from potential extension-related threats. By following this advisory, organizations can take proactive steps to mitigate browser extension risks, enhancing their overall cybersecurity posture.
Reference:
https://www.bleepingcomputer.com/news/security/new-details-reveal-how-hackers-hijacked-35-google-chrome-extensions/
https://learn.microsoft.com/en-us/defender-endpoint/manage-profiles-approve-sys-extensions-intune
https://gbhackers.com/malicious-editthiscookie-extension/#google_vignette
Disclaimer
The information contained in this document is meant to provide general guidance and brief information to the intended recipient pertaining to the incident and recommended action. Therefore, this information is provided "as is" without warranties of any kind, express or implied, including accuracy, timeliness, and completeness. Consequently, under NO condition shall CTM360®, its related partners, directors, principals, agents, or employees be liable for any direct, indirect, accidental, special, exemplary, punitive, consequential, or other damages or claims whatsoever including, but not limited to: loss of data, loss in profits/business, network disruption…etc., arising out of or in connection with this advisory.
For more information:
Email: monitor@ctm360.com Tel: (+973) 77 360 360

External Attack Surface Management: Protecting Your Organization in the Digital Age
In an increasingly interconnected digital world, organisations face a growing number of cyber threats. As businesses expand their online presence, their attack surface increases, making it more vulnerable to cyberattacks. This is where External Attack Surface Management (EASM) comes into play.
In this blog, we will explore the concept of EASM, what it includes, its importance, how it differs from security ratings, and what the future holds for this crucial aspect of cybersecurity. Additionally, we’ll discuss how CTM360 HackerView can help your organisation effectively manage its external attack surface.
What is EASM?
External Attack Surface Management (EASM) involves the continuous discovery, monitoring, and management of an organisation’s external-facing digital assets. These assets include websites, IP addresses, cloud services, and any other publicly accessible resources. A comprehensive EASM would also have the organisation’s mobile apps, genuine social media inventory, Executive Management profiles and more. EASM focuses on first building a comprehensive “Digital Asset Register” and next identifying vulnerabilities and potential entry points that could be exploited by malicious actors. By gaining a deep understanding of the external attack surface, organisations can proactively mitigate risks and prevent breaches before they occur.
From the management perspective, EASM is an essential component of a robust cybersecurity strategy. It enables organisations to see their digital footprint from the perspective of an attacker, allowing them to identify and secure weak points that could be targeted.
What is Included in an Organization’s Attack Surface?
An organisation’s attack surface consists of all the external-facing digital assets that could potentially be targeted by cybercriminals. These include:
Domains, Hosts, and Sub-Domains:
An organization’s collection of domains, along with their associated hosts and sub-domains, creates numerous potential entry points for attackers. Each sub-domain may have unique vulnerabilities that can be exploited if not properly secured.
Web Applications:
Public-facing websites and web applications are common targets for attackers seeking to exploit vulnerabilities such as outdated software or weak authentication mechanisms.
Cloud Services:
With the rise of cloud computing, organisations often use cloud-based services for data storage and processing. Misconfigurations or insufficient security measures in these services can expose sensitive information.
IP Addresses:
Public IP addresses can be scanned by attackers to identify open ports or vulnerable services that can be exploited.
Third-Party Integrations:
Organisations often rely on third-party vendors or services that have access to their systems. These integrations can introduce additional vulnerabilities if not properly managed.SSL/TLS Certificates:
Weak or expired certificates can leave encrypted communications vulnerable to interception.
A comprehensive EASM solution would also include -
Inventory of Genuine Social Media Profiles:
An organisation's presence on social media platforms can be targeted by attackers for impersonation or phishing attempts.
Mobile Apps:
Attackers can create rogue mobile apps on third party stores to impersonate trusted brands, with the goal of gaining unauthorised access to information that can be used to commit fraudulent transactions.
Executive Management Names/Profiles:
Attackers may attempt to impersonate an organisation's executive leadership for social engineering attacks.
BIN Numbers:
Payment card information, including BIN (Bank Identification Number) data, can be exposed and used for fraudulent activities.
Environments & Technologies:
The list of technologies and their respective versions visible in the organisation's attack surface can help identify potential vulnerabilities and misconfigurations.
The attack surface also includes shadow IT, which refers to information technology systems implemented by departments outside of the central IT department to circumvent the limitations and restrictions set by the central information systems.
Why is EASM Important?
EASM is critical for several reasons:
1. Technology consolidation
EASM promotes a unified security strategy, enabling organizations to consolidate their ever growing digital assets and stack of technologies and enhance the overall management of external cyber risk.
2. Reducing Attack Surface
Through continuous monitoring and assessment, EASM assists organizations in reducing their attack surface by proactively managing and securing external assets.
3. Proactive Risk Management:
EASM allows organisations to identify vulnerabilities before they are exploited. By continuously monitoring the attack surface, organisations can address security gaps promptly, reducing the likelihood of a successful attack.
4. Real-Time Visibility:
Cyber threats are constantly evolving, and new vulnerabilities emerge regularly. EASM provides real-time visibility into an organisation’s external assets, ensuring that security teams are always aware of the current state of the attack surface.
5. Regulatory Compliance:
Many industries are subject to strict regulatory requirements regarding data protection and cybersecurity. EASM helps organisations maintain compliance by ensuring that all external assets are properly secured.
6. Cost Efficiency:
Preventing a cyberattack is often far less expensive than dealing with the aftermath of a breach. EASM enables organisations to allocate resources more efficiently by prioritising the most critical vulnerabilities.
How is EASM Different from Security Ratings?
While both EASM and security ratings play a role in assessing an organisation’s cybersecurity posture, they serve different purposes and offer distinct benefits:
1. Scope of Analysis:
Security ratings are typically based on a broad assessment of an organisation’s overall security practices, often using data from public sources. EASM, on the other hand, focuses specifically on the external attack surface, providing a more detailed and targeted analysis of potential vulnerabilities.
2. Continuous Monitoring:
EASM involves continuous monitoring of external assets, offering real-time insights into the attack surface. Security ratings are often static, providing a snapshot of an organisation’s security posture at a specific point in time.
3. Actionable Insights:
EASM provides actionable insights that organisations can use to address specific vulnerabilities. Security ratings are more generalised and may not offer the same level of detail needed to implement targeted security measures.
4. Perspective:
EASM approaches cybersecurity from the attacker’s perspective, identifying entry points and weaknesses that could be exploited. Security ratings focus on the organisation’s overall security practices and controls.
What Does the Future Hold?
As cyber threats continue to evolve, the importance of EASM will only grow. Organisations are increasingly adopting digital transformation strategies, expanding their digital footprints, and moving more services to the cloud. This expansion introduces new vulnerabilities, making EASM an essential component of any comprehensive cybersecurity strategy.
In the future, we can expect EASM tools and technologies to become more sophisticated, incorporating advanced AI and machine learning algorithms to identify and mitigate risks more effectively. The integration of EASM with other cybersecurity solutions, such as Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR), will provide organisations with a more holistic approach to managing their security posture.
How Can CTM360 HackerView Help?
CTM360’s HackerView is an innovative External Attack Surface Management (EASM) platform designed to give organisations a comprehensive understanding of their digital presence from an attacker’s perspective. By combining automated asset discovery, issue identification, remediation guidelines, security ratings, and third-party risk management, HackerView empowers businesses to proactively defend against potential cyber threats.
Here’s how CTM360 HackerView can significantly enhance your organisation's cybersecurity strategy:
1. Continuous & Automated Digital Asset Discovery
One of the most critical aspects of EASM is the ability to identify and map all external-facing digital assets. HackerView excels in this area by automatically discovering and mapping your organisation’s digital footprint. Operating in a passive and non-intrusive manner, it leverages data available in the public domain to uncover assets that may otherwise be overlooked.
The platform comes pre-populated, ensuring that from the moment you start using it, you have a comprehensive view of your digital assets. This includes websites, IP addresses, cloud services, and more. Automated discovery ensures that no asset is left unmonitored, reducing the risk of shadow IT and other unsecured entry points.
One of the key advantages of HackerView is how often it continuously discovers, updates, and refreshes all assets belonging to the organisation. The platform automatically updates its inventory of digital assets every 24-48 hours, ensuring that your security team has access to the most current and complete information about your attack surface.
2. Comprehensive Digital Risk Scorecard
HackerView provides a detailed digital risk scorecard that assesses your organisation’s visible cyber vulnerabilities. This scorecard is essential for understanding your current security posture and identifying areas that require immediate attention. The scorecard is updated continuously, allowing you to track improvements or new risks as they emerge.
3. Detailed Inventory of Digital Assets
Understanding what you have is the first step toward protecting it. HackerView provides a detailed inventory of your digital assets, allowing you to keep track of all external-facing resources. This inventory is continually updated as new assets are discovered or changes are made, ensuring that your records are always accurate and up-to-6.
4. Remediation Plans & Ongoing Guidance
Identifying vulnerabilities is only half the battle; addressing them effectively is the key to maintaining a robust security posture. HackerView not only identifies issues but also provides detailed remediation plans and ongoing guidance. These plans are tailored to your specific vulnerabilities, offering step-by-step instructions on how to address each issue.
5. Third-Party Risk Monitoring
In today’s interconnected world, organisations rely heavily on third-party vendors and partners. However, these relationships can introduce additional risks if not properly managed. HackerView’s third-party risk monitoring feature allows you to assess the security posture of your vendors, partners, and other third parties with whom you share data or systems.
6. Pre-built and Custom Portfolios
The platform allows you to access pre-built portfolios that include entities from important industry sectors within your geographic region. This allows you to benchmark your organisation's cybersecurity posture against your peers, gaining valuable insights into how you measure up. Additionally, you can create custom portfolios of your key vendors and third-party providers, continuously tracking their security health and potential vulnerabilities.
In conclusion, as organisations continue to navigate the complexities of the digital landscape, EASM will remain a vital component of cybersecurity. By leveraging advanced tools like CTM360 HackerView, businesses can protect their digital assets, stay ahead of potential threats and ensure the security of their operations.

Fraudulent Immigration Scam
Global Fraudulent Scheme Targeting National Immigration Services
Overview
CTM360 has identified a fraudulent scheme involving fake websites targeting National Immigration services globally. The deceiving campaign extends to Electronic Travel Authorization, Evisa, and Electronic Custom Declaration processes. These scams have increased dramatically as more things shifted online and require less paperwork. Scammers take advantage of this by making fake websites. People need to be aware of this and be careful not to get tricked.
These fake websites usually use a basic web design and are hosted on well-known hosting services to look real. Additionally, these fake websites put up disclaimers in fine print stating to be private companies and have no affiliation with any government entities. By doing this, it makes it challenging for the Hosting Providers and Domain Registrars to take action on them.

CTM360 Observations
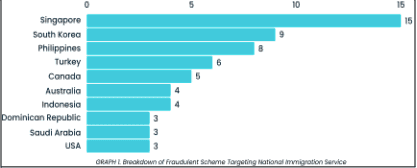
Based on our analysis of the suspicious infrastructure, we believe these fake websites are part of a broader scam campaign targeting multiple immigration services at the same time. Some of the top countries being targeted include Singapore, South Korea, the Philippines, and Turkey. We expect this scam to also occur in other countries in the near future.
The scam initiates with scammers paying for fake ads on search engines, so they show up at the top of search results. They manipulate the search engine algorithms to get their fake sites noticed more easily. This technique makes it more likely for people to accidentally find these fake websites. The ads are constructed in a way that makes the fake sites seem real, so people might trust them without realizing they're being tricked.
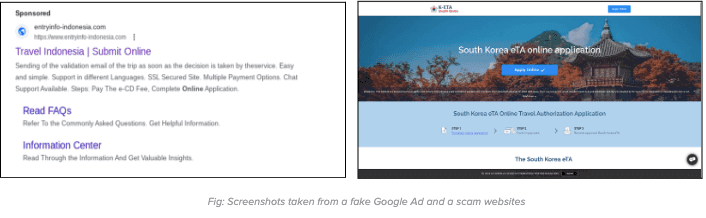
When clicking on the fake ad, users will be redirected to a fake website. On the fake website, they will be prompted to initiate the online visa application process. The process found on the fake website is crafted closely to mimic the procedures found on the official website.
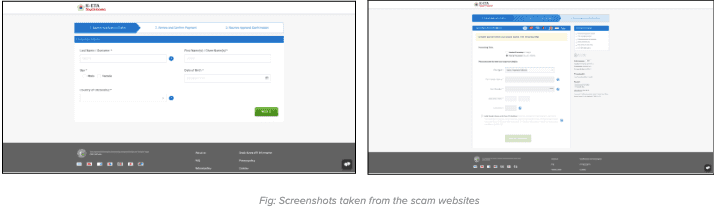
After entering the card details, users will be consistently displayed with error messages falsely claiming payment failures. In reality, the sensitive carding information has already been captured and submitted to the server controlled by the scammers.
Moreover, numerous countries have issued official warnings advising against such fake websites. Please refer to the following sources for more information:
- https://www.cgisf.gov.in/page/important-advisory-on-fake-indian-e-visa-websites/
- https://ircc.canada.ca/english/helpcentre/answer.asp?qnum=1233&top=16
- https://www.perthnow.com.au/news/bali/bali-scam-warning-for-aussie-travellers-to-watch-out-for-fake-websites-providing-counterfeit-visas-c-10513578
- https://www.kenyaembassyaddis.org/2021/06/fraudulent-visa-application-websites/
Recommendations
How to avoid becoming a victim of such scams
For individuals:
- Be very cautious about the sponsored ads specifically about government services.
- When applying for any travel-related services, only use the official website provided by the immigration authorities of the country you're visiting. This may require some research by individuals to ensure they have reached the genuine website.
- Be cautious about clicking on suspicious web URLs, even if they seem to come from people you know.
For Government agencies, ISPs and Domain Registrars:
- Government service providers should publish a list of authorized agents on their websites. This will enable end-users to verify the right provider. Furthermore, it will also provide evidence for the Domain registrar to take prompt action.
- Government agencies are advised to regularly monitor such fake websites that do not have any authorization from the government and update the list of these fake websites on their official portal.
- Government agencies should actively engage with security vendors to identify and take down these fake websites and fake ads.
- There should be national procedures for Local ISPs and National CERTs to block such websites once notified by the right authorities.

Cyber Advisory: Credit/Debit Card Theft via Phishing Campaign Impersonating Known Brands
CTM360 has noticed a surge in phishing websites targeting both local and global brands in the GCC. Scammers are employing a common website design to create phishing pages that imitate the products and logos of these established brands.
OVERVIEW
These phishing campaigns result in significant financial losses and the compromise of personal data for the customers of these brands.
Some well-known brands like Tea Time, Hardees, Jasmis, Caribou, and others are being targeted in this campaign. Because these brands are popular in the GCC and have lots of customers, scammers are going after them. CTM360’s WebHunt platform is actively tracking such phishing campaigns; 100+ phishing sites targeting different brands have been identified as part of this campaign.
CTM360’s observation of the trend
- Mode of Delivery: Fake ads via social media platform
- Scammers have created fake accounts on Facebook and Instagram, which they leverage to promote fake ads with attractive offers from targeted brands. These ads ultimately direct users to phishing sites.

- Scammers then take advantage of users' trust by making these phishing sites on domain names that are related to GCC countries and using the .shop TLD. For instance, they might mix the name of a GCC country with a well-known brand they're copying, like "jasmis-bh- mega-offers[.]shop" or "hardees-kuwait[.]shop". These tricky website addresses are designed to fool users into thinking they're on real websites.
- Brands targeted: The phishing campaign targets major fast food and coffee shops in GCC countries. Scammers create website pages that closely resemble authentic websites, making them appear genuine to unsuspecting individuals. Scammers use a similar phishing layout/template to target various brands.

- Scammers also advertise these websites using flashy promotions, such as "happy hour" images, offering big discounts like 50% off everything and free delivery on orders. This strategy is meant to make users feel like they need to act quickly and tempt them into buying from the fake site.
- Motive: Harvesting Debit/Credit Card Information
- Once the victim has completed adding products to their cart, they are redirected to the payment page, which serves as the motive of the scammer. At this stage, the user is prompted to enter their debit/credit card information to obtain the victim's funds.

Recommendations
How to avoid becoming a victim of such Phishing campaigns:
For individuals:
- Don't click on suspicious URLs, even if they appear from people you know.
- Always verify the official website's appearance and pay attention to the domain name
- and website’s interface.
- Avoid any suspicious resources that ask for personal or payment information.
For businesses:
- Regularly monitor references to your brand in domain name and phishing website databases, which can be accessed by companies that provide brand protection and anti- fraud services.
- Quickly identify and eliminate networks of fraudulent websites that use your brand

Baiting Facebook Groups
CTM360 discovered an ongoing fraudulent activity on Meta's social media platform, ‘Facebook’.
Threat Overview
While conducting fraud hunting exercises, CTM360 discovered an ongoing fraudulent activity on Meta's social media platform, ‘Facebook’. This particular scam involves scammers using Facebook public groups to disseminate fraudulent schemes. These groups are created solely to bait victims. By leveraging these groups, the scammers can reach a large audience that shares common interests or belongs to specific regions. Unfortunately, this fraudulent activity has resulted in financial losses for many unsuspecting individuals.


Fraud Methodology
The scammers begin by either scouting Facebook groups OR creating new groups that serve the scammer's goal, aiming to identify the target audience. This is likely done through various criteria such as:
- Page Topic: the main drive and title that define the overall niche.
- User Interests: the general interest and posts shared in the group by the members.
- Targeted Region: the location where the scammer wants to target the users.
- Scammers are carrying their scams through Facebook and specifically through Facebook groups to abuse its private nature with the ability to mask the profile’s name causing a noticeable rise in fraudulent activities advertised with untraceable users - through the "Anonymous Participant" feature in Facebook Groups.
- Within the suspicious posts, scammers are claiming to provide bogus services like:
- Fraudulent Payment Installments
- Loans or loan restructuring
- Issuance of Credit Cards with high limits
- Fake Job Posting
- Stolen Gift cards
Why Should Organizations Be Concerned?
To reflect legitimacy of the fraudulent promotional post the scammers abuse genuine company name or genuine product brands.
Scammers adopt various tactics, such as presenting themselves as authentic sellers offering enticing deals on products. So they are “impersonating” your organization, brand or identity of your executive management.
Their goal is not to deliver the promised items at all or to provide counterfeit goods. Hence they impersonate well-known brands, celebrities, or even users' friends within these groups, leveraging these false identities to deceive individuals into disclosing sensitive information or making monetary transactions.
One variation of the scam posts claims to host free giveaways or contests. These seemingly attractive offers often serve as a guise to harvest personal information or involve users in deceptive activities. The other scam cases range from inquiries about installment options, salary transfers, credit card applications, loans, and job opportunities to scams like Advance-Fee Fraud.
The unauthorized use of an organization's brand name in posts within such Facebook groups poses a significant concern. At minimum it has implications on reputation, furthermore your customers could suffer financial losses or compromise their personal information, leading to broader implications for both the organization and the affected individuals.
Threat Impacts
The fraudulent posts published in these groups can have various threat impacts on the users such as:
- Financial Loss: These posts often involve fraudulent loan offers that target individuals who are in need of financial assistance. Scammers may request upfront fees or personal information, promising a loan that never materializes.
- Expose Personal Information: When users share personal and financial information in response to fake offers in Facebook groups, there is a risk that this information may be shared or sold to third parties without their consent.
- Phishing Attack: Some loan scams may involve indirect phishing attempts, where scammers might trick individuals into providing their login credentials or other sensitive information through fake loan application forms or websites.
Recommendations
For Businesses:
- Spread Awareness: Conduct awareness campaigns on official social media to educate customers about such scams.
- Active Monitoring & Takedowns of Baiting Facebook Groups: Such baiting groups should be actively monitored and any infringement identified related to your brand should be reported to vendors for further actions such as Takedown.
For Individuals:
- Be cautious with personal information: Avoid sharing personal information in Facebook groups, especially if the posts seem suspicious or potentially fraudulent. Protect your identity and be wary of any requests for sensitive information.
- Don't Pay Upfront Fees: Legitimate lenders typically deduct fees from the loan amount or include them in the repayment plan. Be cautious of these scammers who request upfront fees before providing the loan. This is a common red flag for scams.

A browser-in-the-browser (BitB) attack - Cyber Advisory
A Browser-in-the-Browser (BitB) attack is a sophisticated cyber threat involving injecting malicious code into a victim's web browser.
Threat Overview:
This code creates a secondary browser within the victim's existing browser, allowing the attacker to manipulate web content, intercept network requests, and potentially gain control over the victim's browser and system. Understanding the BitB attack is crucial for organizations to develop effective mitigation strategies.

Once the website is opened, it appears as shown above (this will be the first step).

After enforcing the Full-screen display mode, only the inner browser will appear with the customized URL by the attacker.
Real-Case Scenarios of BitB Attacks:
CTM360 recently observed ongoing attack campaigns utilizing the BitB technique targeting ministries and government websites, specifically the interior ministries.
In the previously mentioned scenario, the official website of MOI Singapore remains unaffected and secure. However, the threat actor is carrying out a phishing attack by creating a fake website. Within this fraudulent site, instead of using traditional phishing methods, such as fake forms or malicious content, the attacker employs a fake browser interface within the phishing site, which appears to be the genuine site for MOI. When the victim accesses the site, they are presented with a full-screen display mode of this embedded browser, which tricks them into submitting their sensitive information.
Attack Methodology
To execute a Browser-in-the-Browser (BitB) attack, the attacker employs tactics to lure the user into visiting a malicious or compromised website. This website contains a phishing page hosted on the attacker's server. The phishing page utilizes JavaScript code to create a simulated browser window, simulating the appearance and behavior of a legitimate browser window. Within this simulated window, various types of fraudulent activities can be displayed.
Moreover, the simulated window displays a URL of the attacker's choice, such as https://accounts.google.com or https://login.microsoftonline.com. This is achieved by modifying the simulated address bar of the pop-up window using JavaScript. It may appear to the user that the specified URL is loaded within the pop-up window, but in reality, it is only shown as an image or text. The user may not notice the absence of SSL certificates or other security indicators typically present in a genuine browser window due to the full-screen display mode, which blocks the appearance of the main website’s URL due to the full-screen display model.
If the user falls victim to the BitB attack and enters their login credentials into the fake login form, the information is sent to the attacker's server via an AJAX request or a concealed form submission. Subsequently, the attacker gains access to the user's account on the legitimate service or proceeds with additional malicious activities such as identity theft or account takeover.
Potential Threats
Browser-in-the-Browser (BitB) attacks pose several potential threats and risks to victims. Here are some of the common threats associated with BitB attacks:
- Data Theft: Attackers can exploit BitB attacks to steal sensitive information, such as login credentials, financial details, personal data, or intellectual property. This stolen data can be used for identity theft, financial fraud, or sold on the dark web.
- Account Takeover: By manipulating the victim's browser and intercepting login credentials, BitB attacks can lead to unauthorized access to the victim's online accounts. Attackers may gain control over email accounts, social media profiles, online banking, or other services, enabling them to impersonate the victim or perform malicious activities.
- Malware Distribution: BitB attacks can be used as a vector to distribute malware onto the victim's system. The secondary browser created by the attacker can be used to download and execute malicious software, potentially leading to further compromise of the victim's device and sensitive data.
- Phishing and Social Engineering: Attackers can utilize BitB attacks to create convincing phishing scenarios. By simulating legitimate websites or services, they trick users into entering their login credentials or other sensitive information, which the attacker then captures and exploits.
Mitigation
The BitB attack is a tricky and risky phishing technique that can trick even careful users and bypass typical security measures. However, there are steps you can take to protect yourself from this attack:
- Be cautious of full-screen prompts: Exercise caution if a website unexpectedly opens a full-screen prompt or overlay. Take a moment to assess the situation and ensure that you are interacting with a legitimate website before entering any sensitive information.
- Be vigilant about website URLs: Pay close attention to the URL before entering any sensitive information. Check for any discrepancies or variations in the domain name or spelling that may indicate a phishing site.
- Pay attention to the details of the pop-up window, such as the size, position, appearance, and behavior of the elements. If something looks off or unusual, you should close the window and report it.
- Use a security-focused browser extension that can detect and block such phishing attempts automatically.
- Keep your browser up to date with the latest security patches and update whenever prompted by your browser.
- Make sure you have 2FA enabled for all of your critical services.
CTM360 is actively monitoring this phishing campaign and taking the necessary action by disrupting the attack and suspending the malicious site/domain. If you encounter any of such malicious sites, please report it to business@ctm360.com.
References

Social Media Account Takeover Fraud
CTM360 has recently observed a spike in the compromise of genuine social media accounts impacting organizations and individuals. The compromise sees the original account holder losing control of their account, and then followers targeted in each successive breach..
These attacks are not seen to be isolated incidents and are part of a campaign that operates based on a network ripple effect. The threat actor targets each compromised account’s followers through social engineering, offering bitcoin or financial investment opportunities. Victims typically treat these posts as genuine as messages originate from within the account holder’s trusted network. Scammers take over your social media account to:
● Pretend to be you and trick the people who follow you.
● Share posts on the account saying they made a lot of money by investing a certain amount.
● Convince the account's followers to share their personal information.
● Lure them with high monetary returns and make them join fake trading platforms that require initial investment.
● Trick the victims into giving away SMS OTP codes sent to their phones, eventually letting the scammers hack the accounts.
● Upon gaining control, the scammer changes all details, including passwords, mobile numbers, and corresponding details.
Commonly known as Social Media Account Takeover Fraud, the evolution of this attack is that it continues to move from account to account, allowing the scammer a window of opportunity to target all followers. This advisory is designed to give you important advice and details on keeping your social media accounts safe and preventing your online connections from becoming targets of these scams. Account takeover fraud isn't restricted to just social media platforms; it can also apply to email accounts, online banking accounts, online shopping accounts, and more. Whilst CTM360 has historically facilitated the process of recovering compromised Instagram accounts for victims with considerable success, there have been policy changes wherein the platforms are increasingly entertaining only direct requests from the original account holder. Recovery for such accounts is challenging for the end-user due to changes in the policies of the social media platforms impacted, notably Instagram and Facebook.
How do scammers take over your social media accounts?
1. Phishing attacks: Through deceptive emails, texts, or calls, they impersonate reputable companies to trick you into divulging sensitive information or visiting phishing sites.
2. Malware Infostealers: Hackers infect your device with software that records your input and sends it to them.
3. Credential stuffing: Scammers use software bots for brute-force attacks on passwords, often evading website security measures.
Recommendations:
- Enabling Two-Factor Authentication (2FA) on all your social media accounts is the best way to minimize risk. Ensure the second factor is linked to your active mobile number, or use an authenticator app with securely stored backup codes.
- For organizations that engage third parties, such as marketing agencies and PR firms, there is elevated risk, and it is recommended to ensure the following: a. Ensure 2FA is a mandatory requirement and emphasize the criticality across all engaged subcontractors. b. Actively audit access of all third-party contractors and ensure a need-basis level of minimum access. Granting administrator privileges is actively discouraged and should reside with an internal stakeholder. c. Do not allow personal accounts of the employees of third parties to be used for handling your organization’s account.
- Exercise caution when it comes to clicking on links shared in messages, even if they appear to be from trusted friends. Be vigilant about potential phishing attempts.
- If 2FA is enabled, do not share One-Time Password (OTP) codes with anyone, including friends and family, unless you are certain it's for a legitimate and known purpose.
- Understand the risks associated with oversharing personal information online. Be mindful of the data you disclose, as malicious actors can exploit it. Protect your privacy by sharing only what's necessary.

Card Loading Schemes on Social Media
We have recently observed various groups on social media platforms where individuals are engaging in the act of “Credit or Debit card loading”, “Bank loading” or “Gift-card loading” etc.
These practices involve inviting individuals to deposit/receive funds through different payment service providers and banking channels. In exchange for their deposits, participants are promised attractive returns or opportunities.
Various individuals were also observed on social media sharing and inquiring about card loading based on BIN numbers referring to loading funds on cards or digital cards based on specific BIN numbers. An example of such posts can be seen in the screenshots below. Since specific BIN ranges are allocated for prepaid or digital cards, these BIN ranges are targeted for loading purposes.

"Loaders" and "Receivers" are terms used to describe the roles of individuals involved in a particular type of scheme. These roles are often associated with money laundering and illegal transfer of funds. Here's what each term means:
Loader: A loader is an individual or group responsible for loading funds onto cards or other payment instruments using various means, including stolen credit card information, compromised bank accounts, or illicitly obtained funds. They may use techniques like credit card bust-out scams or unauthorized transfers to load money onto cards.
Receiver: A receiver is an individual or group who receives the loaded funds, typically through cards, and is responsible for converting or transferring the funds to the fraudsters or the next stage in the money laundering process. The receiver may receive loaded cards, withdraw cash from ATMs, or use the cards to launder the money for purchases.
Risks involved in such Loading / Receiving schemes:
Once the target BINs are identified, funds are transferred or loaded onto the cards or accounts associated with those BINs. Depending on the card's capabilities, the cards or accounts with loaded funds can then be used for various purposes, such as making purchases, online transactions, or ATM withdrawals. Such practices can potentially be abused for fraudulent purposes leading to the following:
Credit Card Bust-Out Scams: In a bust-out scam, fraudsters obtain credit cards using stolen identities or fake information. They load these cards with funds, either through illicit means or by taking advantage of introductory offers with low or zero interest rates. Once the cards are loaded, they quickly max out the credit limit and disappear without making any payments. This leaves the legitimate cardholder or the card issuer responsible for the debt.
Money Laundering: Criminals may use credit card loading to launder money obtained through illegal activities. They load illicitly gained funds onto cards and then use those cards for legitimate purchases or withdrawals, making it difficult for law enforcement to trace the origin of the money.
Money Mule Accounts: Illegally obtained card details or hacked accounts may be exploited to transfer funds to a mule account controlled by fraudsters swiftly. Subsequently, the funds are instantaneously dispersed to various colluding recipients, who, in turn, forward the money or convert it to cash, thereby complicating the money trail and evading detection by anti-money laundering (AML) systems.
Various loading/receiving schemes that we have observed are as follows:
- Bank account Loading
- Credit or Debit Card Loading
- Crypto Loading
- Gift card or prepaid card Loading
- Paypal / Sendwave Loading
It's important to note that credit/debit card loading itself is not inherently fraudulent. Many legitimate uses exist, such as loading funds onto cards for personal budgeting or gifting purposes. However, it is crucial for individuals and financial institutions to be vigilant about potential abuse and to implement security measures to prevent fraudulent activities.
Recommendations:
To protect financial institutions and customers from fraudulent activities involving loaders and receivers, here are some recommendations they can implement:
- Raise awareness by issuing notices on official channels to the customers to avoid such card-loading practices.
- Educate customers about the risks of loading/receiving funds from unknown sources or through suspicious methods. Encourage them to report any unauthorized or suspicious transactions promptly.
- Strengthen identity verification processes when opening new accounts, issuing prepaid cards, or processing transactions. This includes using multi-factor authentication and conducting thorough background checks on customers to detect potential fraudulent actors.

A Closer Look at Gaming Ads Misusing Bank Logos
Recently, CTM360 has observed a surge in fake ads misusing the logos of prominent Banks in the Middle East. These deceptive ads have found their way onto popular social media platforms, including Facebook and Instagram, where they promote gaming mobile applications.
The deceptive nature of these fraudulent ads lies in their use of authentic bank logos, enticing unsuspecting users with the promise of substantial winnings. Such misleading tactics create a false perception, leading users to believe that these reputable financial institutions are somehow affiliated with the promoted gaming apps.
Upon further investigation, it appears that the advertised gaming apps are linked to gambling activities. While these apps present themselves as kid-friendly and suitable for all audiences on the App stores, users who installed these apps were subsequently redirected to casino or betting websites.
CTM360 has detected more than 140+ fake ads on Facebook and Instagram targeting users in the Middle East in the last week. These fake ads redirect users to five distinct mobile applications centered around casino and betting games (refer to Appendix for details). Notably, four of these applications have secured listings on the Apple App Store, while the fifth is available for download on Google Play.

Once the user clicks on the given link, they will be redirected to the app store. The primary target of these fake ads primarily comprises IOS users, therefore Android and Windows users will be redirected to an irrelevant website if they click the given link.
This campaign of fraudulent ads has significantly boosted the download rates of these apps, resulting in their ascent to prominent rankings within the ‘casino’ category on the Apple App Store. Below we have listed the app’s ranking based on countries on the Apple App Store at the time of making this report.

Recommendations
CTM360 has successfully taken down 60+ fake ads from Facebook and Instagram targeting the brand names of Middle East Banks. Additionally below are remediation steps that can be taken to stop the overwhelming amount of fraudulent ads and unregulated gambling apps:
- Run a social media campaign to alert customers about such fake apps and ads.
- Unlicensed and unregulated casino/betting apps should be banned from the Application stores in the country to prevent the general public from falling victim to such apps.
Appendix
List of casino and betting game apps found on official stores.


Quishing / QR code Phishing
CTM360 has observed a recent scam tactic involving phishing emails that use QR codes. This scam represents a prevalent phishing variant where individuals scanning the QR code are directed to a fake login page that closely mimics a legitimate email service.
What is QR Code Phishing?
QR code phishing involves the malicious use of Quick Response (QR) codes to redirect unsuspecting users to fraudulent websites, capture sensitive information, or install malware on their devices. QR codes, which are commonly used for convenient access to various digital content, can be manipulated by cybercriminals to mislead and exploit victims.
Types of QR Code Phishing:
- Malicious QR Codes: Attackers can generate and place their QR codes in public spaces or on fake promotional materials. These QR codes may lead to fake websites that mimic legitimate ones, designed to steal your personal information.
- Overlay Attacks: Cybercriminals can create a malicious overlay on top of a legitimate QR code, leading users to a fraudulent website or application. This overlay can be placed on physical objects like posters or product packaging.
- Fake App Downloads: Attackers may encourage users to scan a QR code to download a malicious application that mimics a legitimate service. These fake apps can compromise your device and steal sensitive data.
Why do Threat Actors Use QR Code Phishing?
QR codes are particularly effective in these attacks as they can evade standard email security measures, including URL scanners, making it difficult to detect any signs of a suspicious link or attachment in the messages the QR code is pasted in. This allows attackers to bypass email protections and trick unsuspecting victims into providing their login credentials or other sensitive information.
Example of the Attack:
The attacker generates a legitimate QR code by claiming that your email password has expired. They distribute the QR code through different channels, including email, social media, or even physical flyers.

When the victim scans the code using their smartphone or other devices, it redirects them to a malicious website that resembles a genuine site. The website prompts the victim to enter their login credentials, which the attacker can then steal and use for malicious purposes.

Recommendations:
- Always verify the source and authenticity of QR codes before scanning them. Use official company websites or trusted sources to obtain QR codes. Be cautious when scanning codes from unknown or unsolicited sources.
- Raise awareness among employees and individuals about QR code phishing risks. Conduct regular training sessions to educate them on safe QR code practices, including verifying the source and checking URLs.
- Before scanning a QR code, take a moment to inspect the associated URL or website address. Look for unusual or suspicious elements such as misspellings, extra characters, or unfamiliar domains.
- Be extremely cautious when a QR code takes you to a website that asks for your personal information, login credentials, or payment.
- Make sure to enable two-factor authentication to enhance the security of your accounts and protect them from unauthorized access.

Unrestricted Resource Consumption
Introduction
API keys are crucial for controlling and monitoring access to APIs. However, their misconfiguration can lead to severe security issues. Exposing API keys externally and failing to set proper restrictions are the most common misconfigurations. These misconfigurations can result in potential risks such as unauthorized access to sensitive data, illegitimate requests, resource consumption, and significant costs. In this advisory, we will examine these issues and provide guidance on identifying and preventing them, using Google API key as an example.
In the context of Google products, API keys serve as authentication credentials. They are unique alphanumeric strings that associate your Google billing account with your project and grant access to specific APIs or SDKs (Software Development Kits).
Issue
If a Google API key that has no restrictions is made public in a source code, it can be used by bad actors to gain unauthorized access to Google APIs using your or your application's identity.
Impact
The impact of a compromised Google API key:
- A compromised API key can lead to financial loss through unauthorized consumption of resources on your account.
- Attackers can use your API key to access your online services and cause service disruption.
- Unauthorized API usage can cause your application to malfunction, potentially affecting user experience.
- Recovering from a compromised API key can be time-consuming and resource-intensive, potentially disrupting your workflow.
How to Exploit
- Find public Google API key(s) in source code. Most commonly, Google maps integrations have the highest possibility of being exposed.
- Check if the key(s) have permissions or restrictions set to them by using them in API queries (Consult the documentation at https://developers.google.com/maps/documentation for possible API enumerations like routes or directions). If a key is vulnerable, the API should respond with the expected data (i.e.: street directions, addresses, image of location).
- If interested in possible incurred costs, consult the Google maps platform pricing at https://mapsplatform.google.com/pricing/ to calculate the cost of using the APIs that the key(s) allow(s).
How To Resolve
To prevent this from happening, it is important to properly secure and restrict access to your API keys through your management console. This can include limiting access to the keys to allow certain API usage, certain applications, restricting the budget, regularly monitoring API key usage, and revoking any keys that have been compromised or are no longer needed. By taking these steps, you can help ensure the security of your API keys and prevent unauthorized and unintentional costs from being incurred.
https://developers.google.com/maps/api-security-best-practices

Phishing Campaigns Abusing IPFS
IPFS is a decentralized system for storing and accessing files, and it has gained popularity due to its potential to improve the efficiency and security of file sharing. However, like any new technology, it also comes with its own set of risks and challenges.
Due to its decentralized nature, threat actors use IPFS to host fake websites, as the files are stored on multiple nodes, rather than on a central server. This makes it challenging to take down the fake website since no central authority can be contacted to remove the website. Furthermore, IPFS websites can be accessed through a content identifier (CID) (a unique string of letters and numbers) which is a label used to point towards the content in IPFS rather than a traditional URL, which can make it more difficult for victims to recognize a phishing attempt.
When a file is uploaded to IPFS, it is split into smaller parts and distributed across different nodes. Each part has a separate hash, which helps the network identify different parts of the file on different nodes. In order to retrieve the files, the hash is entered into the browser. Once identified, the IPFS requests all the parts of the file through a P2P connection. Even if the file is deleted from one node, it can still be accessible on other nodes. IPFS URLs often follow this format:
hxxps://ipfs[.]io/ipfs/{46 random character string}#{user email address}hxxps://ipfs[.]io/ipfs/{46 random character string}?filename={file name}.html &emailtoken={email address}hxxps://ipfs[.]io/ipfs/{46 random character string}?(filename|key)={random character string}
The content stored within the IPFS network can be accessed using IPFS nodes called ‘gateways’ which act as a bridge between the HTTP protocol used by all the web browsers and the IPFS network. The gateways can be set up by anyone using various publicly available tools. The most popular gateways used are the ipfs.io ,Fleek, Dweb.link. Other publicly available IPFS gateways can be found in Appendix.
Various Phishing cases observed on IPFS
Below are some phishing cases observed using IPFS services:
Sharing IPFS links through emails
Phishing attacks are carried out by attackers using social engineering techniques to lure the victim into clicking a link or file embedded in the email. The email contains an IPFS link or an embedded HTML file that looks like a legitimate site, such as Microsoft or DHL. URL Observed:
hxxps\[:]//ipfs\[.]io/ipfs/bafybeibgsqc62urteqhu2l3bq3mql5j2sceysff6wyf5kgqvl7ixiq3icm/ef\[.]html

HTML File hosted on IPFS
In another case, CTM360 has witnessed threat actors utilizing HTML files in their phishing attacks. The HTML file redirects the victims in turn to the destination URL hosted in the IPFS network for stealing their credentials. Upon opening the file, the user is redirected to a document page asking for login credentials.
URL Observed
hxxps://ipfs\[.]fleek\[.]co/ipfs/QmVpwAbNJ8tQUH9h9qTuvaMy5678E6eHmyetKqdanPTSL/#adminiev

IPFS hosted phishing exploiting Google Translate service
Scammers have also implemented a technique where the Google Translate service is being abused. Google Translate lets you translate entire websites simply by passing it a link and selecting the source and target languages. Therefore, it can pose a fake “good” reputation for the websites due to the abuse of Google's official domain, and hence, getting it fraudcasted on safe browsing is also challenging since it is associated with a genuine Google service. Phishing URL:
hxxps\\[:]//z4db4kcmazkuxame2l2iy42m7yf5b2mysb7lqepzngrhk33a-ipfs-dweb-link\\[.]translate\\[.]goog/ML\\[.]html?victim@victim.com+&\_x_tr_hp=bafybeifjos&\_x_tr_sl=auto&\_x_tr_tl=en-GB&\_x_tr_hl=en-GB
Conclusion
By integrating the idea of decentralized cloud services with IPFS, phishing tactics have advanced significantly. This malicious usage of IPFS is expected to rise further, highlighting the importance of being cautious. Organizations need to provide regular training and awareness programs that will educate employees and their customers on new phishing techniques, how to spot and report different phishing cases. Further, blocking identified phishing URL patterns could also mitigate some risks.

Navigating The Risks Of ChatGPT On Financial Institutions
What is ChatGPT?
ChatGPT, an advanced AI language model created by OpenAI, is gaining popularity and attention for its ability to generate human-like responses to natural language input. Trained on large amounts of data, ChatGPT's context comprehension and relevant response generation have made it a popular choice for businesses seeking to enhance customer experience and operations.
Major technology corporations are making significant investments in Artificial Intelligence (AI). Microsoft, for instance, has declared that it will invest $10 billion in OpenAI and intends to merge ChatGPT into its Azure OpenAI suite. This will allow businesses to include AI assets, including DALL-E, a program that generates images, and Codex, which transforms natural language into code, in their technology infrastructure.
While ChatGPT has several benefits for financial institutions, such as improving customer service and automating certain tasks, it also carries some risks that need to be addressed. Major banks and other institutions in the US have banned the use of ChatGPT within the organization. Concerns over sensitive information being put into the chatbot.

Risks associated with incorporating ChatGPT
Let's delve into the potential risks that are currently being debated regarding the use of ChatGPT:
- Data Exposure: One potential risk of using ChatGPT in the workplace is the inadvertent exposure of sensitive data. For example, employees using ChatGPT to generate data insights and analyze large amounts of financial data could unknowingly reveal confidential information while conversing with the AI model, which could lead to breaches of privacy or security. Another known data exposure case observed is Employees could potentially expose private code if they inadvertently include confidential information in the training data. This could occur if an employee includes code snippets that contain sensitive data or proprietary information, such as API keys or login credentials.
- Misinformation: ChatGPT can generate inaccurate or biased responses based on its programming and training data. Financial professionals should be cautious while using it to avoid spreading misinformation or relying on unreliable advice. ChatGPT’s current version was only trained on data sets available through 2021. In addition, the tool pulls online data that isn’t always accurate.
- Technology Dependency: While ChatGPT offers useful insights for financial decision-making, relying solely on technology may overlook human judgment and intuition. Financial professionals may misunderstand ChatGPT's recommendations or become over-reliant on it. Thus, maintaining a balance between technology and human expertise is crucial.
- Privacy Concerns: ChatGPT gathers a lot of personal data that users, unassumingly, might provide. Most AI models need a lot of data to be trained and improved, similarly, organizations might have to process a massive amount of data to train ChatGPT. This can pose a significant risk to individuals and organizations if the information is exposed or used maliciously.
External Risks associated with ChatGPT
- Social Engineering: Cybercriminals can use ChatGPT to impersonate individuals or organizations and create highly personalized and convincing phishing emails, making it difficult for victims to detect the attack. This can lead to successful phishing attacks and increase the likelihood of individuals falling for the scam.
- Creating malicious scripts and malware: Cybercriminals can train ChatGPT on vast amounts of code to produce undetectable malware strains that can bypass traditional security defenses. By using polymorphic techniques like encryption and obfuscation, this malware can dynamically alter its code and behavior, making it challenging to analyze and identify.
Recommendations:
- Financial institutions should establish clear policies and guidelines for using ChatGPT in the workplace to safeguard confidential information and mitigate the risks of data exposure.
- Anonymized data should be used to train an AI model to protect the privacy of individuals and organizations whose data is being used.
- Specific controls should be applied to how employees use information from ChatGPT in connection with their work.
- Awareness training should be provided to Employees who have access to ChatGPT on the potential risks associated with the use of the technology, including the risks of data exposure, privacy violations, and ethical concerns.
- Restricting access to ChatGPT will limit the potential for data exposure and misuse of the technology.

OTP/SMS Flood Attack
We have received multiple reports regarding the growing threat of OTP/SMS flood attacks targeting businesses in the Kingdom of Saudi Arabia (KSA). Attackers are exploiting SMS interfaces to send a large volume of One-Time Passwords (OTPs) or SMS messages to overwhelm the host servers, potentially denying access to legitimate services.

An OTP (One-Time Password) flood attack is a type of Denial-of-Service (DoS) attack that targets the corporate website's contact form, which often includes a field for users to enter their phone number or email address.
Here's how it works:
- The attacker uses automated software or a botnet to send a large volume of messages to the website's contact form, filling in the phone number field with a fake or random entry.
- The website's server receives a flood of incoming requests, each containing a fake or random phone number. The server attempts to process each request.
- The flood of incoming requests can overwhelm the website's server, causing it to slow down or crash, potentially leading to a denial of service for legitimate users.
In some cases, the flood of incoming requests can cause additional strain on the website's server, leading to increased data usage, additional charges, or other financial harm.
POSSIBLE IMPACT
SMS flood attacks can be disruptive and damaging for businesses, leading to loss of productivity, revenue, and reputation. It is important for businesses to have robust cybersecurity measures in place to prevent and mitigate the impact of such attacks. The possible impact may include but is not limited to:
- Poor website performance due to high CPU and memory usage
- Leakage of users’ data and loss of customers trust
- Account hacking and fraudulent transactions
- Disruption of business operations
RECOMMENDATIONS
To mitigate an OTP flood attack, there are a few key measures you can take:
Implement rate limiting: To prevent an attacker from overwhelming the system with a large number of OTP requests, you can implement rate limiting on the number of requests per user or IP address. This can help to prevent a single user from generating too many requests and causing a DoS.
Implement CAPTCHAs or other challenge-response mechanisms: To prevent automated bots from generating a large number of OTP requests, you can implement CAPTCHAs or other challenge-response mechanisms that require the user to pass a robot check.
Monitor system logs: Regularly monitoring system logs can help you detect and respond to suspicious activities, such as a large number of OTP requests from a single user or IP address.
Educate users: Providing users with information about OTP flood attacks and how to protect themselves can help to prevent successful attacks. This can include information on how to recognize suspicious requests and how to report them to the service provider. In many of these cases, a business may choose to leverage the use of an SMS/OTP gateway service to manage these operations.
- A gateway may have guards in place to account for many cases of abuse that can happen against these operations (sending, etc..). They allow to set of budget limits or limit the number of messages per second, minute, hour, or day.
- On the other hand, an application communicating with an SMS gateway should implement a few guards itself in case some restrictions are not applicable. Digital forms that precede requests heading for the SMS gateway should not allow for replay attacks as well as brute force attacks, by use of a CSRF token and/or CAPTCHAs.
- There should be ways to detect any such attempt of attacks as well as to mitigate any implications that may follow.
- When such attacks are detected, offending IP addresses should be blocked from communicating with the applications. The use of WAF appliances can also help reduce the chance of the risk of web application attacks.
- Use two-factor authentication: Two-factor authentication provides an additional layer of security and can help prevent unauthorized access to accounts.
By implementing the above measures, you can reduce the risk of an OTP flood attack and help protect your users and your business from the negative impact of such attacks.

Why Me? - Target Of Phishing Attacks
Introduction
Businesses around the world might differ in operating industry, sector, and geographic location. However, almost all businesses are united in the suffering of phishing attacks targeting their users. Such attacks could be easy to spot by tech-savvy users. Nevertheless, a sophisticated phishing attack could even trick trained users, posing a critical threat and forming a great chance for threat actors to achieve their goals. Moreover, one of the most interesting elements is the variation of the targets, as some users were observed to receive a large volume of phishing emails, while others are receiving a relatively less amount. This advisory aims to uncover the most used techniques by threat actors to obtain the email addresses of the organization’s users to initiate the phishing campaign.
Sources of Email Addresses
Publicly Exposed Accounts
In this case, the threat actors attempt to obtain the email addresses of the users belonging to the targeted entities by searching for any mailboxes associated with the entity's domain in search engines, public resources, and deep web resources such as paste sites. Users in many cases are unintentionally exposing their business emails in LinkedIn or Github accounts as a communication means. However, threat actors will always take advantage of such exposed details to target the users. Additionally, organizations should abstain from publishing content that contains users’ email addresses. The email addresses that can be published are the generic accounts that represent organization departments such as info, HR, marketing, and legal mailboxes.
B2B Directory
A B2B business directory is basically an online directory that is listing businesses around the world, categorizing businesses, and collecting their contact details; aiming to guide users and help them in their search for companies for marketing/business purposes. However, services such RocketReach, Zoominfo, Apollo, Hunter, and SignalHire are truly a goldmine for malicious actors to obtain a user's contact details. These online databases of businesses have their own methodologies for obtaining, verifying, and then selling the employees’ contact details of an entity. B2B directories provide such information for business purposes; hence, most of them also provide a “removal request” feature in their platform so the targeted entity will be allowed to contact them in order to remove their own data from the B2B Directory platform. In the Appendix, we have listed the most common B2B Directory platforms along with their contact details to request the removal of the organization’s details.
Email Syntax Guessing
In this case, the attacker is capable of guessing multiple user mailboxes, either by searching for the email format used by a specific entity or by guessing the generic department's mail lists, such as Public Relations, IT Department, or HR. In this case, the threat actor is not looking for a specific email account; instead, the goal here is to identify the email format being adopted by an organization. Then, the threat actor will work on identifying the employee’s names from public sources such as LinkedIn and map the employee’s name to the organization’s email format. For example, the threat actor was able to identify that the email format followed by XYZ organization is “{First Initial}.{Last Name}@xyz.com”. Then, by exploring the LinkedIn page of XYZ organization, the actor was able to find an employee with the name “John Smith”. Therefore, the threat actor will attempt to target this specific user by sending the phishing email to the mailbox “jsmith@xyz.com” which will likely be a valid email address for the user.
Third-Party Data Breaches
Data breaches are the leakage of an organization's sensitive information, including the Personally Identifiable Information (PII) related to the organization’s users or customers. The breached information is not limited in most cases to email addresses or passwords. Breaches can include the exposure of dates of birth, geographic locations, names, employer name, gender, and phone numbers. Once a third-party entity - such as social media or any service provider - is breached, the malicious actor will tend to sell the data to the public. Such data exposure represents a great source of information for threat actors as for sure some information of the organization's employees will be part of such breaches due to the registration in the breached party. By acquiring the dumps of data breaches and looking for the details associated with the users belonging to the targeted entity, this method can be utilized by the attackers to perform more sophisticated attacks. Users that are using their corporate email accounts for the registration of third-party services are for sure highly vulnerable to this type of information exposure.
Phenomenon: Targeting Personal Inboxes With CxO Name
CTM360 witnessed an increase in a sophisticated attack willing to lure the victims by delivering the phishing email to the victim’s personal inbox. Hence, the victim would be in a tough situation where he might be in a direct encounter with the threat actor; far away from the corporate defenses. The attack scheme is mostly utilizing compromised mailboxes from well-reputed email providers, using a C-level executive name as a sender, and requesting urgent action to be performed from the victim. Such details are actually aligned with the scope of advisory, where the attacker is taking advantage of the exposed details in data breaches, which includes useful information such as email addresses, job titles, employers, names, phone numbers, and social media profiles. Then, the attacker is mapping and correlating these exposed details to the victim profile of the targeted entity and initiates the Phishing attack targeting the victim’s personal mailbox.
Recommendations
In order to protect your organization from email exposure, the following steps are recommended to be taken:
- Ask your employees to remove their business account details if it was published online.
- Reach out to the B2B directories listing your users requesting the removal of the accounts.
- Use generic mailboxes in your online publications such as HR, Marketing, or Legal.
- Ensure to have a strict policy regarding the registration in online third-party services.
- Ensure not to use the same email address pattern across the organization. Use different email patterns such as:
- {LastName}@xyz.com
- {First_Initail}{LastName}@xyz.com
- {FirstName}{LastName}@xyz.com
- {LastName}{First_Initial}{Middle_Initial}@xyz.com
Appendix


CXO Fraud - Scam Emails Originating From Virgin Media, Optimum And Cox.Net
There is an ongoing scam email campaign targeting executives from prominent organizations around the world. These reported email addresses on the domains are genuine email accounts of 'Virgin Media', 'Optimum' & 'Cox communications' users' which are compromised and sold on underground forums. Scammers buy and use such accounts as they have a higher reputation compared to newly created free accounts to bypass email gateways and spam filters and also lower their risk of being detected or tracked back in a bigger BEC attack.
These accounts are compromised by threat actors via phishing emails and malware, and the issue with such accounts will persist as long as end users are not careful enough while dealing with phishing and malicious emails. Based on our previous experience in response with the hosts Virgin Media, Optimum and Cox.net which are TV and cable providers in the UK and USA. They do not investigate email accounts reported to their abuse team without the original email and header information as this is a mandatory requirement as per their abuse policies. However, once this information is provided they do take action by resetting/recovering the reported account of the original user.
Additionally, enabling strict quarantine measures on your email gateway from these domains will make you a harder target and eventually the attackers moving on to another one.
RECOMMENDATIONS
- As a precautionary measure, all email from private and/or external email addresses which contain the name of your executive staff in the "From" field may flagged.
- As part of containment, please ensure to quarantine emails from the domain @virginmedia[.]com, @optimum[.]net, @optonline[.]net, @cox[.]net, @cox[.]com
- As this type of email is tricky, it is highly recommended to conduct phishing awareness training for all employees to avoid potential risks.

CTM360 Hardening Guidelines
Log4j vulnerability (CVE-2021-44228) allows unauthenticated remote code execution and is triggered when a specially crafted string provided by the attacker through a variety of different input vectors, is parsed and processed by the Log4j vulnerable component. Microsoft stated that a vast majority of post-exploitation activities had been observed and based on the nature of the vulnerability, once an attacker has full access and control of an application, they can perform a myriad of objectives including installing coin miners, Cobalt Strike to enable credential theft and lateral movement as well as exfiltrating data from compromised systems. Relevant to Log4j vulnerability below are the most common MITRE ATT@CK Techniques that an attacker may leverage to compromise systems.
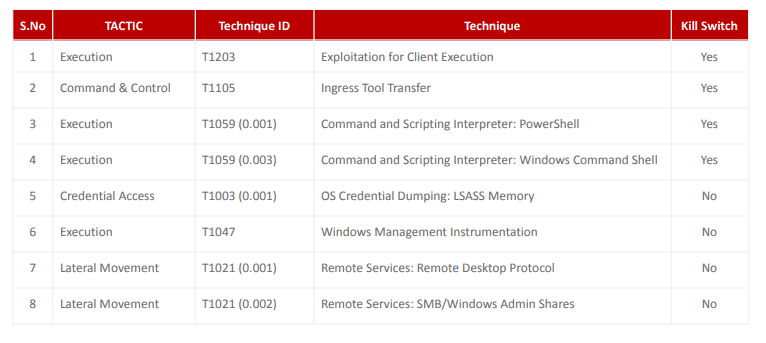
TECHNIQUE#1 - Exploitation for Client Execution
Adversaries may exploit software vulnerabilities in client applications to execute code. Vulnerabilities can exist in software due to insecure coding practices that can lead to unanticipated behavior. Adversaries can take advantage of certain vulnerabilities through targeted exploitation for the purpose of arbitrary code execution.
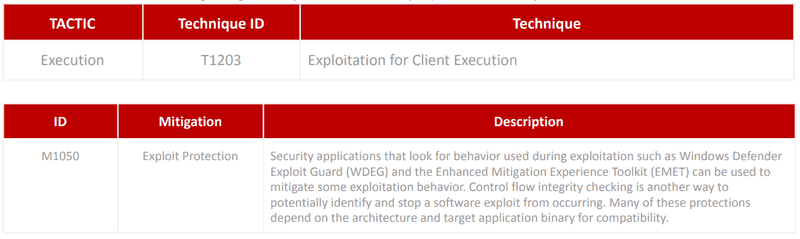
CTM360: Mitigation Guidelines:
Note: Before disabling a service/configuration, please check if any endpoint requires it for a specific use case and only allow it where necessary.
Option 1:
Enable ASR (Attack Surface Reduction) from Group Policy: By leveraging MS ASR rules and relevant IDs to block specific actions from executing on Desktop or Server
Open Group Policy Editor [Local/Domain] click Computer Configuration > Policies > Administrative templates > Windows components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Attack surface reduction.
On Right Side double click on “Configure Attack surface reduction rules” and select Enabled.
Now under options: click on the Show… button and the Show Contents windows will Open.
In Value Name type the below IDs and set the Value to 1 for each rule and click OK to save settings.
Block execution of potentially obfuscated scripts
ID = 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC Value = 1Block JavaScript or VBScript from launching downloaded executable content
ID = D3E037E1-3EB8-44C8-A917-57927947596D Value = 1Block Office application from creating child processes
ID = d4f940ab-401b-4efc-aadc-ad5f3c50688a Value = 1Block Office applications from injecting code into other processes
ID = 75668c1f-73b5-4cf0-bb93-3ecf5cb7cc84 Value = 1Block Win32 API calls from Office macros
ID = 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b Value = 1
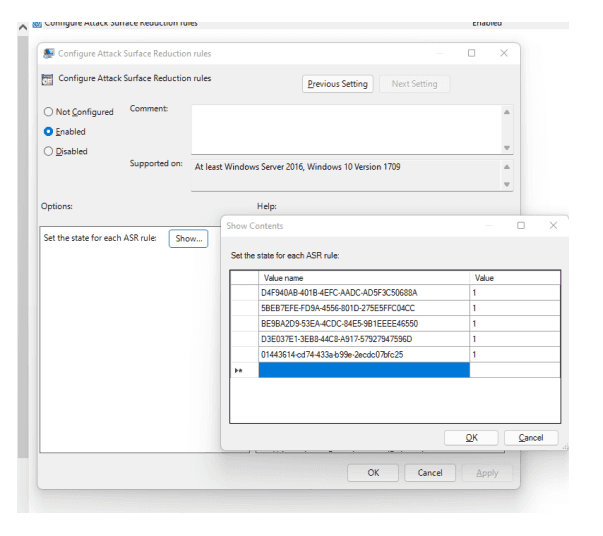
Option 2:
Block Office Macros From Group Policy
(Below steps for Microsoft office 2016/2019) Install the Office 2016 Administrative Template files (ADMX/ADML) and Office Customization Tool on the Active Directory Domain Controller Upon completing the installation, follow the steps below: (For office2016, download the templates from Microsoft. Download link)
Open Group Policy Editor[Local/Domain] > User Configuration > Policies > Administrative templates > Microsoft Word 2016 > Word options > Security > Trust Center
On the right side double click on “Block macros from running in Office files from the Internet” and select Enabled > Click OK to save settings. Double click on “VBA Macro Notification Settings” and select Enabled
Under options select "Disable all without notification" from the drop-down list. Note: Follow the above steps to disable Macros for other Microsoft Office Applications like Excel, PowerPoint etc.)
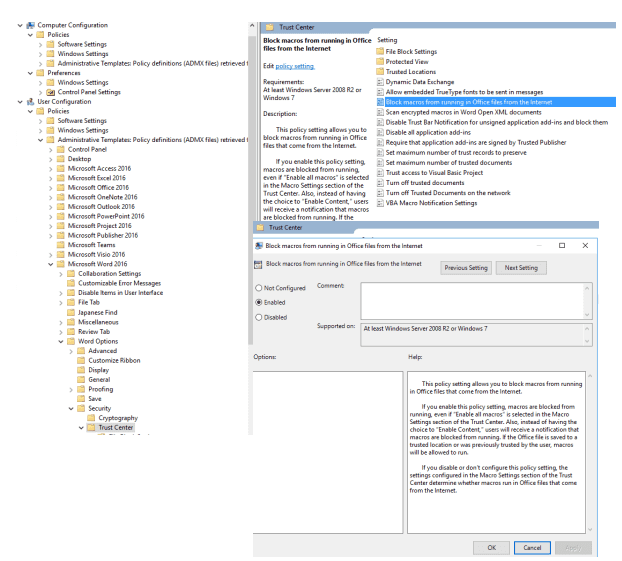
Option 3:
Enable Controlled Folder Access Controlled folder access helps protect your valuable data from malicious apps and threats, such as ransomware. Open Group Policy Editor[Local/Domain] > Computer Configuration > Policies > Administrative Templates > Windows components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Controlled folder access
On the right side window double click on “Configure Controlled folder access” and select Enabled
Under options > Configure the guard my folders feature Select Block from the drop-down list and Click OK to Save Settings. This is a strict mode where untrusted apps cannot make any changes to files inside protected folders.
Note: Enable this with caution as it may affect the organization’s productivity
- TECHNIQUE#2 - Ingress Tool Transfer
- TECHNIQUE#3 - Command and Scripting Interpreter: PowerShell
- TECHNIQUE#4 - Command and Scripting Interpreter: Windows Command Shell
- TECHNIQUE#5 - OS Credential Dumping: LSASS Memory
- TECHNIQUE#6 - Windows Management Instrumentation
- TECHNIQUE#7 - Remote Services: Remote Desktop Protocol
- TECHNIQUE#8 - Remote Services: SMB/Windows Admin Shares
Recommendations
This hardening guide is part of CTM360’s ongoing strategy to provide actionable insights and tangible recommendations for major ransomware families. Our research team will be sharing such advisories frequently to ensure organizations globally become a harder target and can prevent the impact of ransomware proactively. We invite your feedback and welcome your input for future editions of our security hardening series. Kindly reach out to monitor@ctm360.com for any communication.

WhatsApp Account Hijacking
CTM360 has observed a sudden rise in Whatsapp accounts being hijacked in the MENA Region. In most cases, this occurs through social engineering, in which the victim would receive a Whatsapp message or phone call; they are usually requested to provide verification codes or personal/confidential information. Such disclosure would enable the hijackers to take over their victims’ Whatsapp accounts.
Following these occurrences, scammers could then use these accounts to impersonate the victim or even Whatsapp’s support team, usually to send suspicious links to unsuspecting users, or further implement social engineering techniques on other potential victims.
ALTERNATE METHODS USED TO HIJACK WATSAPP ACCOUNTS
CTM360 has observed a sudden rise in Whatsapp accounts being hijacked in the MENA Region. In most cases, this occurs through social engineering, in which the victim would receive a Whatsapp message or phone call; they are usually requested to provide verification codes or personal/confidential information. Such disclosure would enable the hijackers to take over their victims’ Whatsapp accounts.
Following these occurrences, scammers could then use these accounts to impersonate the victim or even Whatsapp’s support team, usually to send suspicious links to unsuspecting users, or further implement social engineering techniques on other potential victims.
Alternate methods used to hijack watsapp accounts
Although most attacks occur through social engineering, many scammers had deviated from their traditional methods. Some key examples may include but are not limited to:
- Brand impersonation: Big brands may often be targeted, e.g. banks and financial institutions, to display a sense of legitimacy. Threat actors may often use a well-known brand image claiming to be from a reputable company. With a convincing display, it wouldn’t take much effort to attain trust and obtain confidential information from victims.
- High profile Impersonation: Scammers may often choose to impersonate C-level executives of large, well-known organizations and other well-known influential personalities. Assuming the character of high profile individuals may convey a sense of importance to the victim, and perhaps invoke a sense of urgency to respond and comply with any given requests.
- Hijacked Whatsapp Accounts: Scammers may use hijacked Whatsapp accounts to send malicious links or requests to the previous account owner’s contacts. Since the contacts are already connected with the victim, the sense of trust may be used to the scammer’s advantage.
- Fake Promotions: Fraudsters may often send links or messages containing information regarding special promotions on fake E-commerce sites. These sites would often lure their victims into providing their WhatsApp registration codes.
- Compromising Victims Voicemail Using Default Password: Scammers may bypass the Whatsapp verification process with the help of the target's voicemail account. This is done when the hacker repeatedly fails the registration code and Whatsapp performs a voice verification by calling the victim directly. By initiating the attack at odd hours, scammers would be able to redirect the message to the victim’s voicemail, which the hacker can easily penetrate to recover the audio message. As a result, victims may get their account stolen without even realizing what had happened.
SECURE YOUR WHATSAPP ACCOUNT
WhatsApp users are advised to take necessary precautionary measures to protect themselves from falling victim to attacks. Some of these include:
- Protecting your WhatsApp account by enabling the ‘Two-Step Verification’ feature; is found under the ‘Settings’ tab of your WhatsApp application. Users may also enable the option of a backup email address if they wish.
- Changing your default voicemail PIN. Please refer to your respective Telco service providers for information on changing/resetting your voicemail PIN.
- Do not share your WhatsApp account verification codes or any One-Time Passwords (OTP) with anyone. You may receive suspicious messages from existing contacts or strangers via WhatsApp. Do not respond, especially if the sender requests an OTP or code. Also do not click on any links or provide any personal information.
- Verify the authenticity of the messages through alternative means (e.g. calling the contact, online research etc.) If the suspicious messages are from unknown numbers, report the contact to WhatsApp directly.

Do you need a Threat Intel feed of IOCs?
Given that your current security stack (AntiVirus, Firewall, SIEM, etc.) already comes integrated with its own auto-updated IOC feeds, do you still need an additional IOC threat intel feed?
Cyber Security is an ever-growing challenge where security teams have to deliver within limited resources and time. Thereby, in the current era of information overload, an effective Cyber Security strategy has to address how to steer away from TIN (Threat Intelligence Noise). Indicators of compromise (IOCs) are the golden factor that enables most of the security technologies to function. Any IP, Domain, URL/Host or file hash that is associated with the malicious activity is introduced as a periodic update to relevant security technologies, enabling detection and blocking of any event that is found attempting to associate with those IOCs.
The daily number of IOCs being discovered across the Cybersecurity industry is mind-boggling. As per AlienVault, their OTX platform provides open access to a global community of threat researchers and security professionals. It now has more than 100,000 participants in 140 countries, who contribute over 19 million threat indicators daily’
The sheer volume shows that it has to be an automated process where the IOCs need to be produced, aggregated, validated and finally, updated into products in a timely manner. Relevant security vendors must do so for the proper functioning of their products.
As for the corporate businesses that are consumers of security products, they are already leveraging IOCs from multiple vendors. Namely, Endpoint security, Perimeter Firewall, IDS/IPS, Email & Web firewall and a SIEM. All these vendors are producing and sharing their IOCs with their peers and each has an auto-update feature in their products.
Now comes the big question. How much extra value would a business gain by investing in a separate cyber threat Intel feed of IOCs and taking on the operational overhead to inject the same across their security products. What will determine that their current product vendors are in fact missing on these IOCs?
BEWARE: There have been situations where a group of non-security business organizations established a platform to share IOCs among themselves. These IOCs may come from unreliable threat feeds and even many times from totally unknown sources. The first question here is how do you establish qualification & validation of those IOCs? The second more important question is, are these IOCs, in fact, unique/new? (not available in the updates of the industries leading security product vendors).
These questions need a well thought out answer before an investment is made into procuring an independent Threat Intelligence feed or a sharing platform of IOCs. The measurement would be by assessing the number of times these IOCs were unique AND they were discovered inside your network affiliated with malicious events. The other approach would be just to ensure that your current security technology stack is configured for timely updates. Specifically, ensure that your SIEM is leveraging from IOC feeds that are already part of your current investments.

Solar Wind Attack Update
SolarWinds - an American software vendor for managing networks and infrastructure has been breached. Orion, a network monitoring product was modified by a state-sponsored threat actor via embedding backdoor code into a legitimate SolarWinds library. This allowed remote access into the victim’s environment and a foothold in their networks; this enabled attacker to obtain privileged credentials.
The SolarWinds Orion products are designed to monitor the networks of systems and report on any security issues. Due to this, there are no comparable limiting boundaries on the scope or potential security impact; this has been made clear by the gradual revelation of more and more high-value targets. Even more worrisome is the fact that the attackers apparently made use of their initial access to targeted organizations, such as FireEye and Microsoft, to compromise tools and code that would then enable them to target other victims. After Microsoft discovered that they were breached via the SolarWinds compromise, they further discovered that their own products were then used “to further the attacks on others.”
The attack was initially disclosed by the cybersecurity firm, FireEye, as early as December 8th but published publicly on 13th. It was revealed that the attack on SolarWinds was conducted by an unknown APT (Advanced Persistent Threat) group. They were able to steal Red Team assessment tools, similarly, used by FireEye to probe its customers’ security. FireEye has made its countermeasures freely available on GitHub.
According to Microsoft, hackers acquired superuser access to SAML token-signing certificates. This SAML certificate was then used to forge new tokens to allow hackers to obtain trusted and highly privileged access to networks.
While analyzing further on this attack, it was discovered that there was another backdoor likely from a second threat actor. This malware was dubbed as SUPERNOVA. This was a web shell planted in the code of the Orion network and applications monitoring platform and enabled attackers to run arbitrary code on machines running the trojanized version of the software.

Hackers inserted malicious code into an updated version of the software, called Orion. Approximately 18,000 SolarWinds customers installed tainted updates, between March and June 2020, onto their systems. The malware was inserted in these Orion app versions:
- Orion Platform 2019.4 HF5, version 2019.4.5200.9083
- Orion Platform 2020.2 RC1, version 2020.2.100.12219
- Orion Platform 2020.2 RC2, version 2020.2.5200.12394
- Orion Platform 2020.2, 2020.2 HF1, version 2020.2.5300.12432
This disclosure was followed by a coordinated report issued by Microsoft, FireEye, SolarWinds, and the U.S. government. The report concluded that SolarWinds had been targeted by threat actors who aimed to gather undisclosed information from major customers of theirs, including FireEye.
Compromise: What is Known so Far
A key indicator of the attack was the conceived backdoor that was able to gain access to and breach the SolarWinds Orion build system. This backdoor was attached to the said system by rescripting the legitimate SolarWinds.Orion.Core.BusinessLayer.dll DLL file. This file was then distributed to SolarWinds’ clients in a supply chain attack. This was achieved due to an automatic update platform used to dispense new software updates; clients were unaware of this taking place.
According to reports, the threat actors may have performed trial runs of the distribution method as early as October 2019. Researchers believe that the attackers had already compromised networks previously; it is suggested that they had harvested information or performed other malicious activities silently for months. Due to this, FireEye eventually detected that they were hacked after the threat actors registered a device to the company’s multi-factor authentication (MFA) system using stolen credentials. The alert from the system, regarding an unknown device, was able to notify FireEye of the compromise.
Recommendations
Urgently update any exploited SolarWinds Orion software to Orion Platform version 2020.2.1 HF 2 and Orion Platform 2019.4 HF 6
Third party vendors who may be susceptible to exposure of this compromise should report as part of responsible disclosure and urgently remediate.
In case of possible exposure devise an incident response plan.
Prioritize the TTPs leveraged by the threat actor mapped to mitre att&ck. This is available in Adversary Intelligence within CTM360’s CyberBlindspot.

WordPress Pharma Hack
Pharma Hack is an exploit targeting WordPress sites using SEO spamming. Hackers inject the site with content related to pharmaceuticals in order to lure users who are looking for drug resellers either to purchase without a prescription or get a cheaper price. Attackers hijack well established sites to bypass Google’s efforts in delisting websites offering to engage in illegal drug sales.
HOW TO IDENTIFY IF A WEBSITE IS PHARMA HACKED?
Pharma Hacks can be tricky to discover because the hack is not visible to the website owner. The only way to view these are through search engines when a user is looking for specific drugs. Hackers target sites that rank high and have a massive amount of traffic for better earnings prospects.

Key indicators that a site has been infected with the hack would include an unusual decrease or increase in traffic for no apparent reason. Google might remove your site from the search results for suspicious behavior. To help identify those scams you can use a security plugin to scan your site or opt for a manual scan which could be more challenging.
COMMON WORDPRESS VULNERABILITIES
WordPress themes and plugins unfortunately are flawed with vulnerabilities. Even though patches are released as an update, there is a possibility of clients running outdated versions. WordPress has tried to resolve this issue using the Auto-update feature.
WordPress site owners tend to use ‘easy to remember’ username and passwords or retain the default username ‘admin’. This along with not implementing Two Factor Authentication invites brute force attacks.
Many website owners still run on HTTP and not HTTPS, which makes intercepting connection on the website easy for attackers. It is vital to install SSL certificates.
Hackers look for highly ranked websites such as banking websites that attract a high volume of traffic, in order to use the website for further goals such as spreading malware, hacktivism, adding bandwidth to bot networks used in DDOS attacks or merely for practice runs. The lack of sensitive information on your website does not ensures your safety. Instead you need to take the necessary security measures to ensure your protection against attacks.
Recommendations
- Update to the newest version of your CMS along with the plugins
- Always use and download legitimate themes and plugins and make sure the auto-update is enabled.
- Set complex credentials for login along with Two Factor Authentication (2FA).
- Make sure SSL Certificates are installed.
- Identify and block any unusual traffic.

Importance Of Verification On Social Media Platforms
Why should you get your account verified?
Team CTM360 takes action on hundreds of fake profiles daily and part of the requirements to take down such profiles is to provide the host with the genuine profile of the individual or brand that is being impersonated. Social media hosts are able to shut down the fake profiles faster if the impersonated individual or brand has a verified account on their platform.
Moreover, this helps people verify that they have found the intended account they are searching for, at a glance they’ll be able to differentiate between a fan account and a genuine account of the individual or brand they’re looking for. A verified account is also a status symbol and a way to establish brand credibility online. Within a world of fake news and widespread media mistrust, verification of social media accounts will be more critical than ever in 2020.
Benefits of verified accounts
- It helps your page show up higher in search results so that potential customers can easily find your account.
- Some platforms offer verified users access to more tools.
- This verified checkmark will help others trust your brand
Who can get verified?
Only real individuals, registered businesses, or brands can apply to get their accounts verified. Not all social media platforms give the same priority or standards for their verified account but what they all have in common is the fact that they grant a verified badge to notable accounts that are in the public interest and have a high likelihood of being impersonated.
Guidelines to verifying your account on different social media platforms
The process varies from one host to another as they require different documentation and have different standards to which they hold up their verified accounts.
Facebook:
For faster response to your verification application make sure your account follows these requisites:
- The applicant's profile must look professional, ensure you are only sharing on-brand content to your Page, and remove anything that negatively affects your credibility
- The applicant's profile information must be up to date
- Link the profile to official properties (the official website and other verified accounts on different platforms)
- The applicant's profile must be very detailed, including phone number, addresses, mission statements, company overview and other social media accounts in the ‘About’ section
Application Process:
- Click on Settings at the top of your Facebook Page
- From the General menu, click the Page Verification selection
- Click on Verify this Page, then Get Started
- You will have the option for an instant or more detailed verification process. Instant verification which will allow Facebook to call you and give you a verification code to enter in the box Facebook provides you with. Detailed verification click on ‘Verify this Page with documents’. When prompted, upload a picture of the official document that clearly shows your business’s name and address.
- Once Facebook receives your validation they will review and either confirm or deny your request. This process usually takes anywhere from 48 hours to 45 days.
Twitter:
Before filling the verification form there are a couple of steps that would help your account be more eligible for verification. Make sure all your information is up to date so that Twitter does not ask you to resubmit the application. This information includes profile picture and header, the title of work, description, location, birthday (for personal accounts). You should also specify a website for others to see you in action and set your tweets as public.
Application Process:
- Access the request form, enter the username of the account you want to get verified
- Proceed to fill the form with the required information
- If Twitter approves your request, you will receive a Direct Message on your Twitter account.
Instagram:
Make sure your Instagram account complies with the following terms of service & community guidelines before submitting your form to ensure a higher rate of success:
- The applicant must be authentic (real individual or legitimate brand)
- The applicant must be unique, only one account per individual or brand can get verified (with exceptions for language-specific accounts)
- The applicant account must be public
- The applicant account must be complete with a profile photo, a complete bio, and at least one post
- The applicant must be someone notable; a highly searched for individual, brand, or entity
Application Process:
- Log into the account you want to get verified.
- Tap the menu icon in the top right corner of your profile.
- Tap Settings > Request Verification.
- Fill in the following fields (Account Username, Full Name, Known As, Category)
- Upload a copy of your government-issued photo ID or an official business document For individuals: driver’s license, passport, or government-issued identity card. For business: tax return, a utility bill in your company name, or your articles of incorporation.
- Instagram will review your application for verification once you send it.
- Instagram will notify you whether your request is approved or denied. You’ll receive the message in your Instagram notifications. This generally takes a couple of days.
YouTube:
For a channel to be verified it must first hit 100,000 subscribers but that itself may not qualify your channel for the verification badge. YouTube takes other things into consideration when granting their verification badge so it is important that you comply with the following:
- For brand related channels, link your website to your channel, this shows that your channel represents a brand and is more credible
- Make sure to abide by YouTubes policies as any previous violations or account suspension will make it harder for the channel to get verified
- Upload quality content regularly to your channel
Application Process:
- Go to Google's support page
- Click on ‘Contact flow’, where you will find the eligibility section. (your channel must have at least 100,000 subscribers for it to be eligible)
- Choose ‘Email Support’
- Fill out the form
- Submit the form, YouTube takes around 24 hours to respond if your request has been approved or denied.
Pinterest:
Application Process:
- Upgrade to a business account
- From the settings, click claim and enter your website
- Add the HTML tag Pinterest gives you to your website’s backend script area
- Submit your request for review




