Microsoft Mandates DMARC for Bulk Email by May2025


What’s on this page
Overview
The fight against email-based threats is intensifying. Following the lead of Google and Yahoo, Microsoft has officially announced the mandatory implementation of email authentication protocols, SPF, DKIM, and DMARC, for high-volume email senders, effective May 5, 2025. Domains sending over 5,000 daily emails to Microsoft's platforms, including Outlook.com, Hotmail.com, and Live.com, will be required to authenticate their messages. Initially, non-compliant messages will be redirected to recipients' Junk folders, with eventual total rejection expected if compliance isn't achieved. This enforcement represents a critical step in securing global email communications from spoofing and phishing threats (Microsoft Tech Community).
Understanding Email Authentication
Email authentication has become essential in combating increasingly sophisticated phishing and spoofing attacks. Three core standards have been adopted widely:
- Sender Policy Framework (SPF: RFC 7208): Verifies the legitimacy of the sending mail server, ensuring messages originate from authorized infrastructure. SPF helps prevent sender address forgery by defining authorized sending sources in DNS records.

- DomainKeys Identified Mail (DKIM: RFC 6376): Cryptographically signs email messages, allowing recipients to confirm message content hasn't been altered in transit. DKIM leverages public-private key pairs to ensure message integrity and authenticity.
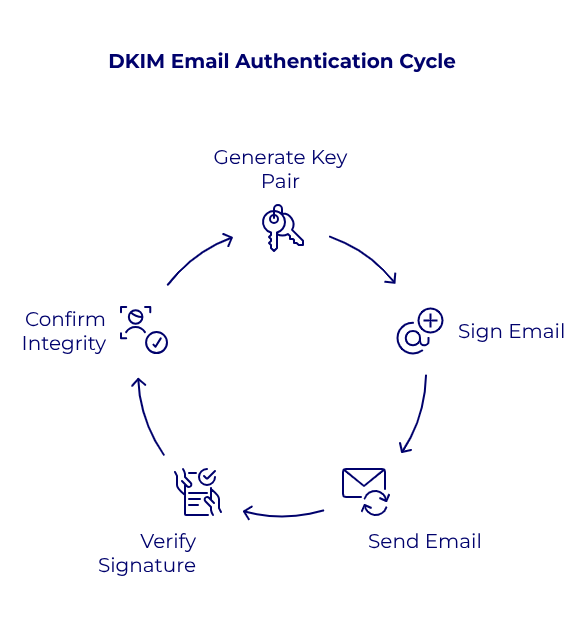
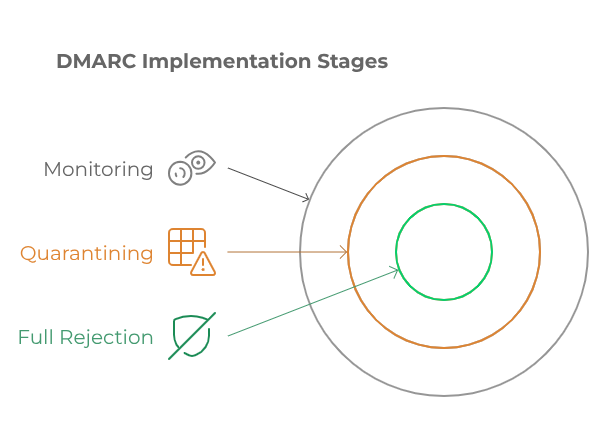
- Domain-based Message Authentication, Reporting, and Conformance (DMARC: RFC 7489): Combines SPF and DKIM to enforce domain alignment, verify authenticity, and provide reporting mechanisms for senders to track email usage and potential abuse. DMARC is recommended to be implemented in three incremental stages: initial monitoring (p=none), intermediate quarantining of suspicious messages to test the policy impact (p=quarantine), and full rejection of unauthorized emails to achieve DMARC compliance (p=reject).
Email Content and Delivery Best Practice Guidance
To help the email ecosystem thrive and ensure that legitimate communications reach users' inboxes, major providers like Google, Yahoo, and Microsoft have released a unified set of technical and content-based requirements. This section consolidates these guidelines into a single resource for senders seeking to avoid spam filtering and maintain high deliverability rates.
1. Message Headers & Structural Integrity
2. Content Hygiene and Formatting
3. Infrastructure and Technical Configuration
4. Recipient List Management
5. Engagement and Complaint Monitoring
6. Summary Recommendations
- Align headers and domains with clear, professional identities.
- Respect opt-in and unsubscribe behaviors with transparent mechanisms.
- Structure content to be clean, concise, and free of deceptive or spammy characteristics.
- Maintain technical hygiene through DNS, TLS, SPF limits, and ARC usage.
- Monitor sender reputation and user engagement continuously.
- Ensure SPF and DKIM are properly configured and aligned with the domain in the
Fromp=none.
Immediate Impact and Risks of Non - compliance
As of May 2025, domains that fail SPF or DKIM checks or lack a correctly configured DMARC policy with alignment will risk having their emails marked as spam or not delivered at all. Misalignment occurs when the domain used in the message's "From" address doesn't match the domains authenticated by SPF or DKIM.
Organizations failing to comply face significant risks, including diminished deliverability rates, compromised customer trust, and increased susceptibility to impersonation attacks. These impacts directly affect an organization's reputation, customer engagement, and potentially, its revenue.
Actionable Recommendations for Immediate Implementation
To effectively prepare for these mandatory standards, organizations should:
- Audit current DNS records: Utilize tools such as "dig" or Google DNS to verify SPF, DKIM, and DMARC records.
- Begin with Monitoring (p=none): Initially deploy DMARC in monitoring mode to understand email flows and detect anomalies without risking legitimate email delivery.
- Gradually enforce stricter policies: Move from quarantine to full rejection while monitoring.
- Ensure domain alignment: "From" domain must match what’s authenticated via SPF or DKIM.
- Maintain email hygiene: Clean lists, include a clear opt-out option, and avoid using misleading subject lines or headers.
Start Your DMARC Journey with CTM360 Free Community Edition
To support organizations navigating these changes, CTM360 offers a complimentary zero-cost Community Edition platform. It allows comprehensive monitoring, management, and enhancement of your DMARC records and email authentication setup. This proactive approach helps organizations reduce risks associated with impersonation attacks and maintain reliable email communication.
Join CTM360 Community Edition today, no hidden costs, simply real security.
Reference:
Disclaimer:
The information contained in this document is meant to provide general guidance and brief information to the intended recipient pertaining to the incident and recommended action. Therefore, this information is provided "as is" without warranties of any kind, express or implied, including accuracy, timeliness, and completeness.
Consequently, under NO condition shall CTM360®, its related partners, directors, principals, agents, or employees be liable for any direct, indirect, accidental, special, exemplary, punitive, consequential, or other damages or claims whatsoever including, but not limited to loss of data, loss in profits/business, network disruption...etc., arisina out of or in connection with this advisory.
For more information: Email: monitor@ctm360.com Tel: (973) 77 360 360
Recent Blogs

Digital Theft
CTM360 has observed a sudden rise in Whatsapp accounts being hijacked in the MENA Region. In most cases, this occurs through social engineering, in which the victim would receive a Whatsapp message or phone call; they are usually requested to provide verification codes or personal/confidential information. Such disclosure would enable the hijackers to take over their victims’ Whatsapp accounts.
Following these occurrences, scammers could then use these accounts to impersonate the victim or even Whatsapp’s support team, usually to send suspicious links to unsuspecting users, or further implement social engineering techniques on other potential victims.
ALTERNATE METHODS USED TO HIJACK WATSAPP ACCOUNTS
CTM360 has observed a sudden rise in Whatsapp accounts being hijacked in the MENA Region. In most cases, this occurs through social engineering, in which the victim would receive a Whatsapp message or phone call; they are usually requested to provide verification codes or personal/confidential information. Such disclosure would enable the hijackers to take over their victims’ Whatsapp accounts.
Following these occurrences, scammers could then use these accounts to impersonate the victim or even Whatsapp’s support team, usually to send suspicious links to unsuspecting users, or further implement social engineering techniques on other potential victims.
Alternate methods used to hijack watsapp accounts
Although most attacks occur through social engineering, many scammers had deviated from their traditional methods. Some key examples may include but are not limited to:
- Brand impersonation: Big brands may often be targeted, e.g. banks and financial institutions, to display a sense of legitimacy. Threat actors may often use a well-known brand image claiming to be from a reputable company. With a convincing display, it wouldn’t take much effort to attain trust and obtain confidential information from victims.
- High profile Impersonation: Scammers may often choose to impersonate C-level executives of large, well-known organizations and other well-known influential personalities. Assuming the character of high profile individuals may convey a sense of importance to the victim, and perhaps invoke a sense of urgency to respond and comply with any given requests.
- Hijacked Whatsapp Accounts: Scammers may use hijacked Whatsapp accounts to send malicious links or requests to the previous account owner’s contacts. Since the contacts are already connected with the victim, the sense of trust may be used to the scammer’s advantage.
- Fake Promotions: Fraudsters may often send links or messages containing information regarding special promotions on fake E-commerce sites. These sites would often lure their victims into providing their WhatsApp registration codes.
- Compromising Victims Voicemail Using Default Password: Scammers may bypass the Whatsapp verification process with the help of the target's voicemail account. This is done when the hacker repeatedly fails the registration code and Whatsapp performs a voice verification by calling the victim directly. By initiating the attack at odd hours, scammers would be able to redirect the message to the victim’s voicemail, which the hacker can easily penetrate to recover the audio message. As a result, victims may get their account stolen without even realizing what had happened.
SECURE YOUR WHATSAPP ACCOUNT
WhatsApp users are advised to take necessary precautionary measures to protect themselves from falling victim to attacks. Some of these include:
- Protecting your WhatsApp account by enabling the ‘Two-Step Verification’ feature; is found under the ‘Settings’ tab of your WhatsApp application. Users may also enable the option of a backup email address if they wish.
- Changing your default voicemail PIN. Please refer to your respective Telco service providers for information on changing/resetting your voicemail PIN.
- Do not share your WhatsApp account verification codes or any One-Time Passwords (OTP) with anyone. You may receive suspicious messages from existing contacts or strangers via WhatsApp. Do not respond, especially if the sender requests an OTP or code. Also do not click on any links or provide any personal information.
- Verify the authenticity of the messages through alternative means (e.g. calling the contact, online research etc.) If the suspicious messages are from unknown numbers, report the contact to WhatsApp directly.

Unrestricted Resource Consumption
Introduction
API keys are crucial for controlling and monitoring access to APIs. However, their misconfiguration can lead to severe security issues. Exposing API keys externally and failing to set proper restrictions are the most common misconfigurations. These misconfigurations can result in potential risks such as unauthorized access to sensitive data, illegitimate requests, resource consumption, and significant costs. In this advisory, we will examine these issues and provide guidance on identifying and preventing them, using Google API key as an example.
In the context of Google products, API keys serve as authentication credentials. They are unique alphanumeric strings that associate your Google billing account with your project and grant access to specific APIs or SDKs (Software Development Kits).
Issue
If a Google API key that has no restrictions is made public in a source code, it can be used by bad actors to gain unauthorized access to Google APIs using your or your application's identity.
Impact
The impact of a compromised Google API key:
- A compromised API key can lead to financial loss through unauthorized consumption of resources on your account.
- Attackers can use your API key to access your online services and cause service disruption.
- Unauthorized API usage can cause your application to malfunction, potentially affecting user experience.
- Recovering from a compromised API key can be time-consuming and resource-intensive, potentially disrupting your workflow.
How to Exploit
- Find public Google API key(s) in source code. Most commonly, Google maps integrations have the highest possibility of being exposed.
- Check if the key(s) have permissions or restrictions set to them by using them in API queries (Consult the documentation at https://developers.google.com/maps/documentation for possible API enumerations like routes or directions). If a key is vulnerable, the API should respond with the expected data (i.e.: street directions, addresses, image of location).
- If interested in possible incurred costs, consult the Google maps platform pricing at https://mapsplatform.google.com/pricing/ to calculate the cost of using the APIs that the key(s) allow(s).
How To Resolve
To prevent this from happening, it is important to properly secure and restrict access to your API keys through your management console. This can include limiting access to the keys to allow certain API usage, certain applications, restricting the budget, regularly monitoring API key usage, and revoking any keys that have been compromised or are no longer needed. By taking these steps, you can help ensure the security of your API keys and prevent unauthorized and unintentional costs from being incurred.
https://developers.google.com/maps/api-security-best-practices

External Attack Surface Management: Protecting Your Organization in the Digital Age
In an increasingly interconnected digital world, organisations face a growing number of cyber threats. As businesses expand their online presence, their attack surface increases, making it more vulnerable to cyberattacks. This is where External Attack Surface Management (EASM) comes into play.
In this blog, we will explore the concept of EASM, what it includes, its importance, how it differs from security ratings, and what the future holds for this crucial aspect of cybersecurity. Additionally, we’ll discuss how CTM360 HackerView can help your organisation effectively manage its external attack surface.
What is EASM?
External Attack Surface Management (EASM) involves the continuous discovery, monitoring, and management of an organisation’s external-facing digital assets. These assets include websites, IP addresses, cloud services, and any other publicly accessible resources. A comprehensive EASM would also have the organisation’s mobile apps, genuine social media inventory, Executive Management profiles and more. EASM focuses on first building a comprehensive “Digital Asset Register” and next identifying vulnerabilities and potential entry points that could be exploited by malicious actors. By gaining a deep understanding of the external attack surface, organisations can proactively mitigate risks and prevent breaches before they occur.
From the management perspective, EASM is an essential component of a robust cybersecurity strategy. It enables organisations to see their digital footprint from the perspective of an attacker, allowing them to identify and secure weak points that could be targeted.
What is Included in an Organization’s Attack Surface?
An organisation’s attack surface consists of all the external-facing digital assets that could potentially be targeted by cybercriminals. These include:
Domains, Hosts, and Sub-Domains:
An organization’s collection of domains, along with their associated hosts and sub-domains, creates numerous potential entry points for attackers. Each sub-domain may have unique vulnerabilities that can be exploited if not properly secured.
Web Applications:
Public-facing websites and web applications are common targets for attackers seeking to exploit vulnerabilities such as outdated software or weak authentication mechanisms.
Cloud Services:
With the rise of cloud computing, organisations often use cloud-based services for data storage and processing. Misconfigurations or insufficient security measures in these services can expose sensitive information.
IP Addresses:
Public IP addresses can be scanned by attackers to identify open ports or vulnerable services that can be exploited.
Third-Party Integrations:
Organisations often rely on third-party vendors or services that have access to their systems. These integrations can introduce additional vulnerabilities if not properly managed.SSL/TLS Certificates:
Weak or expired certificates can leave encrypted communications vulnerable to interception.
A comprehensive EASM solution would also include -
Inventory of Genuine Social Media Profiles:
An organisation's presence on social media platforms can be targeted by attackers for impersonation or phishing attempts.
Mobile Apps:
Attackers can create rogue mobile apps on third party stores to impersonate trusted brands, with the goal of gaining unauthorised access to information that can be used to commit fraudulent transactions.
Executive Management Names/Profiles:
Attackers may attempt to impersonate an organisation's executive leadership for social engineering attacks.
BIN Numbers:
Payment card information, including BIN (Bank Identification Number) data, can be exposed and used for fraudulent activities.
Environments & Technologies:
The list of technologies and their respective versions visible in the organisation's attack surface can help identify potential vulnerabilities and misconfigurations.
The attack surface also includes shadow IT, which refers to information technology systems implemented by departments outside of the central IT department to circumvent the limitations and restrictions set by the central information systems.
Why is EASM Important?
EASM is critical for several reasons:
1. Technology consolidation
EASM promotes a unified security strategy, enabling organizations to consolidate their ever growing digital assets and stack of technologies and enhance the overall management of external cyber risk.
2. Reducing Attack Surface
Through continuous monitoring and assessment, EASM assists organizations in reducing their attack surface by proactively managing and securing external assets.
3. Proactive Risk Management:
EASM allows organisations to identify vulnerabilities before they are exploited. By continuously monitoring the attack surface, organisations can address security gaps promptly, reducing the likelihood of a successful attack.
4. Real-Time Visibility:
Cyber threats are constantly evolving, and new vulnerabilities emerge regularly. EASM provides real-time visibility into an organisation’s external assets, ensuring that security teams are always aware of the current state of the attack surface.
5. Regulatory Compliance:
Many industries are subject to strict regulatory requirements regarding data protection and cybersecurity. EASM helps organisations maintain compliance by ensuring that all external assets are properly secured.
6. Cost Efficiency:
Preventing a cyberattack is often far less expensive than dealing with the aftermath of a breach. EASM enables organisations to allocate resources more efficiently by prioritising the most critical vulnerabilities.
How is EASM Different from Security Ratings?
While both EASM and security ratings play a role in assessing an organisation’s cybersecurity posture, they serve different purposes and offer distinct benefits:
1. Scope of Analysis:
Security ratings are typically based on a broad assessment of an organisation’s overall security practices, often using data from public sources. EASM, on the other hand, focuses specifically on the external attack surface, providing a more detailed and targeted analysis of potential vulnerabilities.
2. Continuous Monitoring:
EASM involves continuous monitoring of external assets, offering real-time insights into the attack surface. Security ratings are often static, providing a snapshot of an organisation’s security posture at a specific point in time.
3. Actionable Insights:
EASM provides actionable insights that organisations can use to address specific vulnerabilities. Security ratings are more generalised and may not offer the same level of detail needed to implement targeted security measures.
4. Perspective:
EASM approaches cybersecurity from the attacker’s perspective, identifying entry points and weaknesses that could be exploited. Security ratings focus on the organisation’s overall security practices and controls.
What Does the Future Hold?
As cyber threats continue to evolve, the importance of EASM will only grow. Organisations are increasingly adopting digital transformation strategies, expanding their digital footprints, and moving more services to the cloud. This expansion introduces new vulnerabilities, making EASM an essential component of any comprehensive cybersecurity strategy.
In the future, we can expect EASM tools and technologies to become more sophisticated, incorporating advanced AI and machine learning algorithms to identify and mitigate risks more effectively. The integration of EASM with other cybersecurity solutions, such as Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR), will provide organisations with a more holistic approach to managing their security posture.
How Can CTM360 HackerView Help?
CTM360’s HackerView is an innovative External Attack Surface Management (EASM) platform designed to give organisations a comprehensive understanding of their digital presence from an attacker’s perspective. By combining automated asset discovery, issue identification, remediation guidelines, security ratings, and third-party risk management, HackerView empowers businesses to proactively defend against potential cyber threats.
Here’s how CTM360 HackerView can significantly enhance your organisation's cybersecurity strategy:
1. Continuous & Automated Digital Asset Discovery
One of the most critical aspects of EASM is the ability to identify and map all external-facing digital assets. HackerView excels in this area by automatically discovering and mapping your organisation’s digital footprint. Operating in a passive and non-intrusive manner, it leverages data available in the public domain to uncover assets that may otherwise be overlooked.
The platform comes pre-populated, ensuring that from the moment you start using it, you have a comprehensive view of your digital assets. This includes websites, IP addresses, cloud services, and more. Automated discovery ensures that no asset is left unmonitored, reducing the risk of shadow IT and other unsecured entry points.
One of the key advantages of HackerView is how often it continuously discovers, updates, and refreshes all assets belonging to the organisation. The platform automatically updates its inventory of digital assets every 24-48 hours, ensuring that your security team has access to the most current and complete information about your attack surface.
2. Comprehensive Digital Risk Scorecard
HackerView provides a detailed digital risk scorecard that assesses your organisation’s visible cyber vulnerabilities. This scorecard is essential for understanding your current security posture and identifying areas that require immediate attention. The scorecard is updated continuously, allowing you to track improvements or new risks as they emerge.
3. Detailed Inventory of Digital Assets
Understanding what you have is the first step toward protecting it. HackerView provides a detailed inventory of your digital assets, allowing you to keep track of all external-facing resources. This inventory is continually updated as new assets are discovered or changes are made, ensuring that your records are always accurate and up-to-6.
4. Remediation Plans & Ongoing Guidance
Identifying vulnerabilities is only half the battle; addressing them effectively is the key to maintaining a robust security posture. HackerView not only identifies issues but also provides detailed remediation plans and ongoing guidance. These plans are tailored to your specific vulnerabilities, offering step-by-step instructions on how to address each issue.
5. Third-Party Risk Monitoring
In today’s interconnected world, organisations rely heavily on third-party vendors and partners. However, these relationships can introduce additional risks if not properly managed. HackerView’s third-party risk monitoring feature allows you to assess the security posture of your vendors, partners, and other third parties with whom you share data or systems.
6. Pre-built and Custom Portfolios
The platform allows you to access pre-built portfolios that include entities from important industry sectors within your geographic region. This allows you to benchmark your organisation's cybersecurity posture against your peers, gaining valuable insights into how you measure up. Additionally, you can create custom portfolios of your key vendors and third-party providers, continuously tracking their security health and potential vulnerabilities.
In conclusion, as organisations continue to navigate the complexities of the digital landscape, EASM will remain a vital component of cybersecurity. By leveraging advanced tools like CTM360 HackerView, businesses can protect their digital assets, stay ahead of potential threats and ensure the security of their operations.



.webp)