Solar Wind Attack Update


What’s on this page
SolarWinds - an American software vendor for managing networks and infrastructure has been breached. Orion, a network monitoring product was modified by a state-sponsored threat actor via embedding backdoor code into a legitimate SolarWinds library. This allowed remote access into the victim’s environment and a foothold in their networks; this enabled attacker to obtain privileged credentials.
The SolarWinds Orion products are designed to monitor the networks of systems and report on any security issues. Due to this, there are no comparable limiting boundaries on the scope or potential security impact; this has been made clear by the gradual revelation of more and more high-value targets. Even more worrisome is the fact that the attackers apparently made use of their initial access to targeted organizations, such as FireEye and Microsoft, to compromise tools and code that would then enable them to target other victims. After Microsoft discovered that they were breached via the SolarWinds compromise, they further discovered that their own products were then used “to further the attacks on others.”
The attack was initially disclosed by the cybersecurity firm, FireEye, as early as December 8th but published publicly on 13th. It was revealed that the attack on SolarWinds was conducted by an unknown APT (Advanced Persistent Threat) group. They were able to steal Red Team assessment tools, similarly, used by FireEye to probe its customers’ security. FireEye has made its countermeasures freely available on GitHub.
According to Microsoft, hackers acquired superuser access to SAML token-signing certificates. This SAML certificate was then used to forge new tokens to allow hackers to obtain trusted and highly privileged access to networks.
While analyzing further on this attack, it was discovered that there was another backdoor likely from a second threat actor. This malware was dubbed as SUPERNOVA. This was a web shell planted in the code of the Orion network and applications monitoring platform and enabled attackers to run arbitrary code on machines running the trojanized version of the software.

Hackers inserted malicious code into an updated version of the software, called Orion. Approximately 18,000 SolarWinds customers installed tainted updates, between March and June 2020, onto their systems. The malware was inserted in these Orion app versions:
- Orion Platform 2019.4 HF5, version 2019.4.5200.9083
- Orion Platform 2020.2 RC1, version 2020.2.100.12219
- Orion Platform 2020.2 RC2, version 2020.2.5200.12394
- Orion Platform 2020.2, 2020.2 HF1, version 2020.2.5300.12432
This disclosure was followed by a coordinated report issued by Microsoft, FireEye, SolarWinds, and the U.S. government. The report concluded that SolarWinds had been targeted by threat actors who aimed to gather undisclosed information from major customers of theirs, including FireEye.
Compromise: What is Known so Far
A key indicator of the attack was the conceived backdoor that was able to gain access to and breach the SolarWinds Orion build system. This backdoor was attached to the said system by rescripting the legitimate SolarWinds.Orion.Core.BusinessLayer.dll DLL file. This file was then distributed to SolarWinds’ clients in a supply chain attack. This was achieved due to an automatic update platform used to dispense new software updates; clients were unaware of this taking place.
According to reports, the threat actors may have performed trial runs of the distribution method as early as October 2019. Researchers believe that the attackers had already compromised networks previously; it is suggested that they had harvested information or performed other malicious activities silently for months. Due to this, FireEye eventually detected that they were hacked after the threat actors registered a device to the company’s multi-factor authentication (MFA) system using stolen credentials. The alert from the system, regarding an unknown device, was able to notify FireEye of the compromise.
Recommendations
Urgently update any exploited SolarWinds Orion software to Orion Platform version 2020.2.1 HF 2 and Orion Platform 2019.4 HF 6
Third party vendors who may be susceptible to exposure of this compromise should report as part of responsible disclosure and urgently remediate.
In case of possible exposure devise an incident response plan.
Prioritize the TTPs leveraged by the threat actor mapped to mitre att&ck. This is available in Adversary Intelligence within CTM360’s CyberBlindspot.
Recent Blogs

Unrestricted Resource Consumption
Introduction
API keys are crucial for controlling and monitoring access to APIs. However, their misconfiguration can lead to severe security issues. Exposing API keys externally and failing to set proper restrictions are the most common misconfigurations. These misconfigurations can result in potential risks such as unauthorized access to sensitive data, illegitimate requests, resource consumption, and significant costs. In this advisory, we will examine these issues and provide guidance on identifying and preventing them, using Google API key as an example.
In the context of Google products, API keys serve as authentication credentials. They are unique alphanumeric strings that associate your Google billing account with your project and grant access to specific APIs or SDKs (Software Development Kits).
Issue
If a Google API key that has no restrictions is made public in a source code, it can be used by bad actors to gain unauthorized access to Google APIs using your or your application's identity.
Impact
The impact of a compromised Google API key:
- A compromised API key can lead to financial loss through unauthorized consumption of resources on your account.
- Attackers can use your API key to access your online services and cause service disruption.
- Unauthorized API usage can cause your application to malfunction, potentially affecting user experience.
- Recovering from a compromised API key can be time-consuming and resource-intensive, potentially disrupting your workflow.
How to Exploit
- Find public Google API key(s) in source code. Most commonly, Google maps integrations have the highest possibility of being exposed.
- Check if the key(s) have permissions or restrictions set to them by using them in API queries (Consult the documentation at https://developers.google.com/maps/documentation for possible API enumerations like routes or directions). If a key is vulnerable, the API should respond with the expected data (i.e.: street directions, addresses, image of location).
- If interested in possible incurred costs, consult the Google maps platform pricing at https://mapsplatform.google.com/pricing/ to calculate the cost of using the APIs that the key(s) allow(s).
How To Resolve
To prevent this from happening, it is important to properly secure and restrict access to your API keys through your management console. This can include limiting access to the keys to allow certain API usage, certain applications, restricting the budget, regularly monitoring API key usage, and revoking any keys that have been compromised or are no longer needed. By taking these steps, you can help ensure the security of your API keys and prevent unauthorized and unintentional costs from being incurred.
https://developers.google.com/maps/api-security-best-practices

External Attack Surface Management: Protecting Your Organization in the Digital Age
In an increasingly interconnected digital world, organisations face a growing number of cyber threats. As businesses expand their online presence, their attack surface increases, making it more vulnerable to cyberattacks. This is where External Attack Surface Management (EASM) comes into play.
In this blog, we will explore the concept of EASM, what it includes, its importance, how it differs from security ratings, and what the future holds for this crucial aspect of cybersecurity. Additionally, we’ll discuss how CTM360 HackerView can help your organisation effectively manage its external attack surface.
What is EASM?
External Attack Surface Management (EASM) involves the continuous discovery, monitoring, and management of an organisation’s external-facing digital assets. These assets include websites, IP addresses, cloud services, and any other publicly accessible resources. A comprehensive EASM would also have the organisation’s mobile apps, genuine social media inventory, Executive Management profiles and more. EASM focuses on first building a comprehensive “Digital Asset Register” and next identifying vulnerabilities and potential entry points that could be exploited by malicious actors. By gaining a deep understanding of the external attack surface, organisations can proactively mitigate risks and prevent breaches before they occur.
From the management perspective, EASM is an essential component of a robust cybersecurity strategy. It enables organisations to see their digital footprint from the perspective of an attacker, allowing them to identify and secure weak points that could be targeted.
What is Included in an Organization’s Attack Surface?
An organisation’s attack surface consists of all the external-facing digital assets that could potentially be targeted by cybercriminals. These include:
Domains, Hosts, and Sub-Domains:
An organization’s collection of domains, along with their associated hosts and sub-domains, creates numerous potential entry points for attackers. Each sub-domain may have unique vulnerabilities that can be exploited if not properly secured.
Web Applications:
Public-facing websites and web applications are common targets for attackers seeking to exploit vulnerabilities such as outdated software or weak authentication mechanisms.
Cloud Services:
With the rise of cloud computing, organisations often use cloud-based services for data storage and processing. Misconfigurations or insufficient security measures in these services can expose sensitive information.
IP Addresses:
Public IP addresses can be scanned by attackers to identify open ports or vulnerable services that can be exploited.
Third-Party Integrations:
Organisations often rely on third-party vendors or services that have access to their systems. These integrations can introduce additional vulnerabilities if not properly managed.SSL/TLS Certificates:
Weak or expired certificates can leave encrypted communications vulnerable to interception.
A comprehensive EASM solution would also include -
Inventory of Genuine Social Media Profiles:
An organisation's presence on social media platforms can be targeted by attackers for impersonation or phishing attempts.
Mobile Apps:
Attackers can create rogue mobile apps on third party stores to impersonate trusted brands, with the goal of gaining unauthorised access to information that can be used to commit fraudulent transactions.
Executive Management Names/Profiles:
Attackers may attempt to impersonate an organisation's executive leadership for social engineering attacks.
BIN Numbers:
Payment card information, including BIN (Bank Identification Number) data, can be exposed and used for fraudulent activities.
Environments & Technologies:
The list of technologies and their respective versions visible in the organisation's attack surface can help identify potential vulnerabilities and misconfigurations.
The attack surface also includes shadow IT, which refers to information technology systems implemented by departments outside of the central IT department to circumvent the limitations and restrictions set by the central information systems.
Why is EASM Important?
EASM is critical for several reasons:
1. Technology consolidation
EASM promotes a unified security strategy, enabling organizations to consolidate their ever growing digital assets and stack of technologies and enhance the overall management of external cyber risk.
2. Reducing Attack Surface
Through continuous monitoring and assessment, EASM assists organizations in reducing their attack surface by proactively managing and securing external assets.
3. Proactive Risk Management:
EASM allows organisations to identify vulnerabilities before they are exploited. By continuously monitoring the attack surface, organisations can address security gaps promptly, reducing the likelihood of a successful attack.
4. Real-Time Visibility:
Cyber threats are constantly evolving, and new vulnerabilities emerge regularly. EASM provides real-time visibility into an organisation’s external assets, ensuring that security teams are always aware of the current state of the attack surface.
5. Regulatory Compliance:
Many industries are subject to strict regulatory requirements regarding data protection and cybersecurity. EASM helps organisations maintain compliance by ensuring that all external assets are properly secured.
6. Cost Efficiency:
Preventing a cyberattack is often far less expensive than dealing with the aftermath of a breach. EASM enables organisations to allocate resources more efficiently by prioritising the most critical vulnerabilities.
How is EASM Different from Security Ratings?
While both EASM and security ratings play a role in assessing an organisation’s cybersecurity posture, they serve different purposes and offer distinct benefits:
1. Scope of Analysis:
Security ratings are typically based on a broad assessment of an organisation’s overall security practices, often using data from public sources. EASM, on the other hand, focuses specifically on the external attack surface, providing a more detailed and targeted analysis of potential vulnerabilities.
2. Continuous Monitoring:
EASM involves continuous monitoring of external assets, offering real-time insights into the attack surface. Security ratings are often static, providing a snapshot of an organisation’s security posture at a specific point in time.
3. Actionable Insights:
EASM provides actionable insights that organisations can use to address specific vulnerabilities. Security ratings are more generalised and may not offer the same level of detail needed to implement targeted security measures.
4. Perspective:
EASM approaches cybersecurity from the attacker’s perspective, identifying entry points and weaknesses that could be exploited. Security ratings focus on the organisation’s overall security practices and controls.
What Does the Future Hold?
As cyber threats continue to evolve, the importance of EASM will only grow. Organisations are increasingly adopting digital transformation strategies, expanding their digital footprints, and moving more services to the cloud. This expansion introduces new vulnerabilities, making EASM an essential component of any comprehensive cybersecurity strategy.
In the future, we can expect EASM tools and technologies to become more sophisticated, incorporating advanced AI and machine learning algorithms to identify and mitigate risks more effectively. The integration of EASM with other cybersecurity solutions, such as Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR), will provide organisations with a more holistic approach to managing their security posture.
How Can CTM360 HackerView Help?
CTM360’s HackerView is an innovative External Attack Surface Management (EASM) platform designed to give organisations a comprehensive understanding of their digital presence from an attacker’s perspective. By combining automated asset discovery, issue identification, remediation guidelines, security ratings, and third-party risk management, HackerView empowers businesses to proactively defend against potential cyber threats.
Here’s how CTM360 HackerView can significantly enhance your organisation's cybersecurity strategy:
1. Continuous & Automated Digital Asset Discovery
One of the most critical aspects of EASM is the ability to identify and map all external-facing digital assets. HackerView excels in this area by automatically discovering and mapping your organisation’s digital footprint. Operating in a passive and non-intrusive manner, it leverages data available in the public domain to uncover assets that may otherwise be overlooked.
The platform comes pre-populated, ensuring that from the moment you start using it, you have a comprehensive view of your digital assets. This includes websites, IP addresses, cloud services, and more. Automated discovery ensures that no asset is left unmonitored, reducing the risk of shadow IT and other unsecured entry points.
One of the key advantages of HackerView is how often it continuously discovers, updates, and refreshes all assets belonging to the organisation. The platform automatically updates its inventory of digital assets every 24-48 hours, ensuring that your security team has access to the most current and complete information about your attack surface.
2. Comprehensive Digital Risk Scorecard
HackerView provides a detailed digital risk scorecard that assesses your organisation’s visible cyber vulnerabilities. This scorecard is essential for understanding your current security posture and identifying areas that require immediate attention. The scorecard is updated continuously, allowing you to track improvements or new risks as they emerge.
3. Detailed Inventory of Digital Assets
Understanding what you have is the first step toward protecting it. HackerView provides a detailed inventory of your digital assets, allowing you to keep track of all external-facing resources. This inventory is continually updated as new assets are discovered or changes are made, ensuring that your records are always accurate and up-to-6.
4. Remediation Plans & Ongoing Guidance
Identifying vulnerabilities is only half the battle; addressing them effectively is the key to maintaining a robust security posture. HackerView not only identifies issues but also provides detailed remediation plans and ongoing guidance. These plans are tailored to your specific vulnerabilities, offering step-by-step instructions on how to address each issue.
5. Third-Party Risk Monitoring
In today’s interconnected world, organisations rely heavily on third-party vendors and partners. However, these relationships can introduce additional risks if not properly managed. HackerView’s third-party risk monitoring feature allows you to assess the security posture of your vendors, partners, and other third parties with whom you share data or systems.
6. Pre-built and Custom Portfolios
The platform allows you to access pre-built portfolios that include entities from important industry sectors within your geographic region. This allows you to benchmark your organisation's cybersecurity posture against your peers, gaining valuable insights into how you measure up. Additionally, you can create custom portfolios of your key vendors and third-party providers, continuously tracking their security health and potential vulnerabilities.
In conclusion, as organisations continue to navigate the complexities of the digital landscape, EASM will remain a vital component of cybersecurity. By leveraging advanced tools like CTM360 HackerView, businesses can protect their digital assets, stay ahead of potential threats and ensure the security of their operations.

Fraudulent Immigration Scam
Global Fraudulent Scheme Targeting National Immigration Services
Overview
CTM360 has identified a fraudulent scheme involving fake websites targeting National Immigration services globally. The deceiving campaign extends to Electronic Travel Authorization, Evisa, and Electronic Custom Declaration processes. These scams have increased dramatically as more things shifted online and require less paperwork. Scammers take advantage of this by making fake websites. People need to be aware of this and be careful not to get tricked.
These fake websites usually use a basic web design and are hosted on well-known hosting services to look real. Additionally, these fake websites put up disclaimers in fine print stating to be private companies and have no affiliation with any government entities. By doing this, it makes it challenging for the Hosting Providers and Domain Registrars to take action on them.

CTM360 Observations
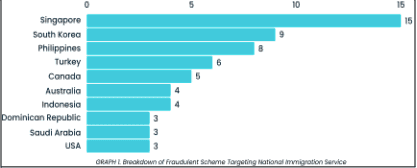
Based on our analysis of the suspicious infrastructure, we believe these fake websites are part of a broader scam campaign targeting multiple immigration services at the same time. Some of the top countries being targeted include Singapore, South Korea, the Philippines, and Turkey. We expect this scam to also occur in other countries in the near future.
The scam initiates with scammers paying for fake ads on search engines, so they show up at the top of search results. They manipulate the search engine algorithms to get their fake sites noticed more easily. This technique makes it more likely for people to accidentally find these fake websites. The ads are constructed in a way that makes the fake sites seem real, so people might trust them without realizing they're being tricked.
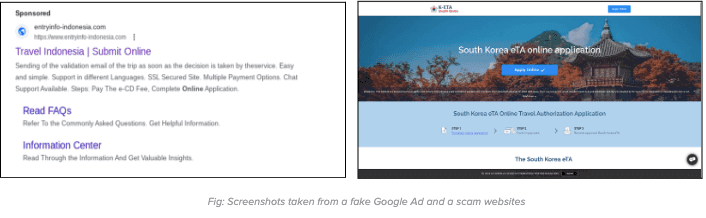
When clicking on the fake ad, users will be redirected to a fake website. On the fake website, they will be prompted to initiate the online visa application process. The process found on the fake website is crafted closely to mimic the procedures found on the official website.
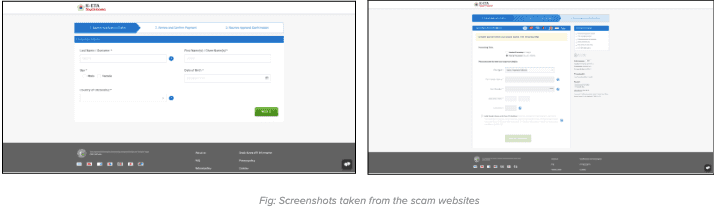
After entering the card details, users will be consistently displayed with error messages falsely claiming payment failures. In reality, the sensitive carding information has already been captured and submitted to the server controlled by the scammers.
Moreover, numerous countries have issued official warnings advising against such fake websites. Please refer to the following sources for more information:
- https://www.cgisf.gov.in/page/important-advisory-on-fake-indian-e-visa-websites/
- https://ircc.canada.ca/english/helpcentre/answer.asp?qnum=1233&top=16
- https://www.perthnow.com.au/news/bali/bali-scam-warning-for-aussie-travellers-to-watch-out-for-fake-websites-providing-counterfeit-visas-c-10513578
- https://www.kenyaembassyaddis.org/2021/06/fraudulent-visa-application-websites/
Recommendations
How to avoid becoming a victim of such scams
For individuals:
- Be very cautious about the sponsored ads specifically about government services.
- When applying for any travel-related services, only use the official website provided by the immigration authorities of the country you're visiting. This may require some research by individuals to ensure they have reached the genuine website.
- Be cautious about clicking on suspicious web URLs, even if they seem to come from people you know.
For Government agencies, ISPs and Domain Registrars:
- Government service providers should publish a list of authorized agents on their websites. This will enable end-users to verify the right provider. Furthermore, it will also provide evidence for the Domain registrar to take prompt action.
- Government agencies are advised to regularly monitor such fake websites that do not have any authorization from the government and update the list of these fake websites on their official portal.
- Government agencies should actively engage with security vendors to identify and take down these fake websites and fake ads.
- There should be national procedures for Local ISPs and National CERTs to block such websites once notified by the right authorities.



