Go Beyond IOCs
and understand how an adversary behaves and operates
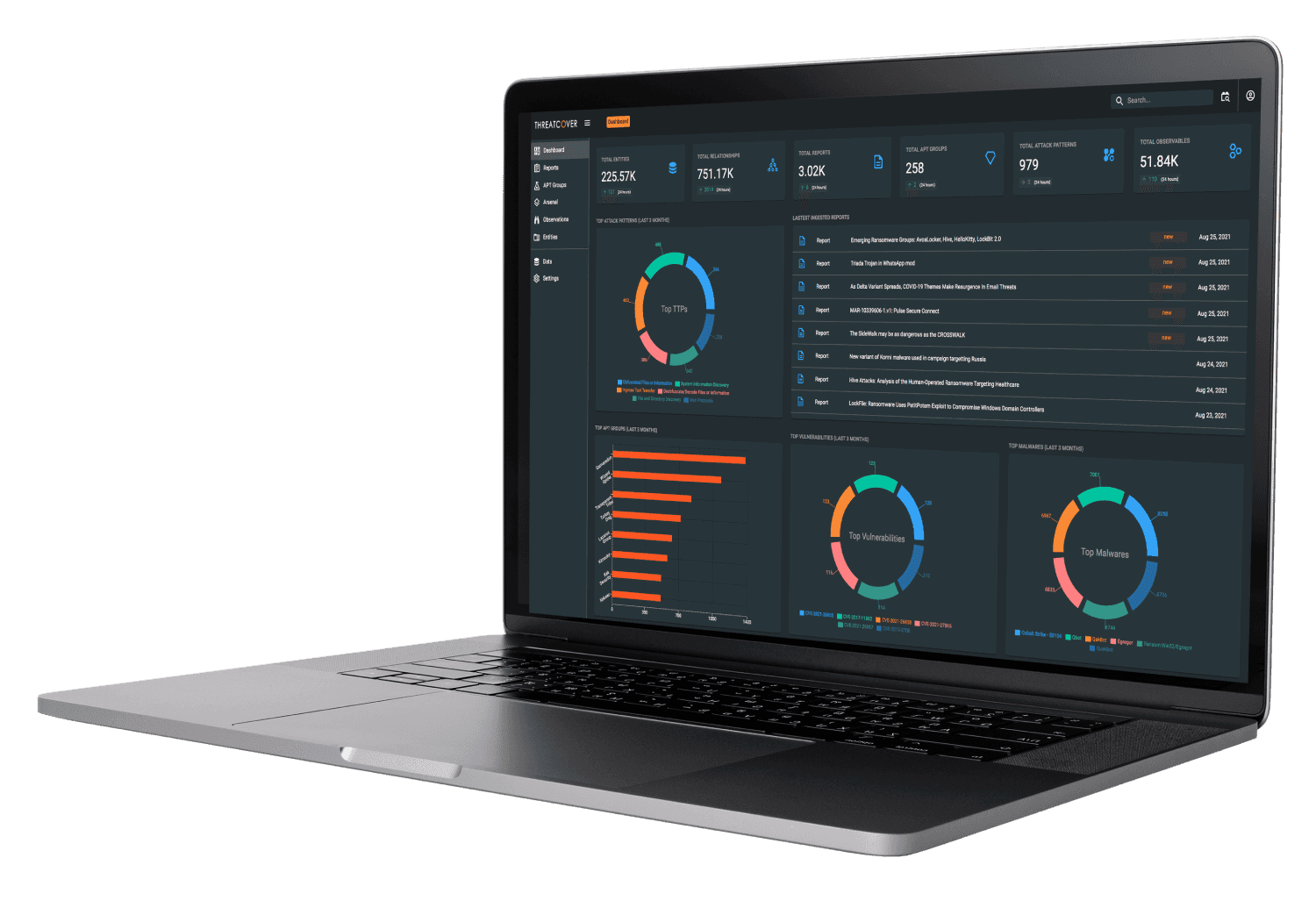
ThreatCover is a Comprehensive Threat Intelligence Platform (TIP) that Empowers Your Team to Efficiently Defend and Respond to the Diverse Range of Threats.
Powered by curated sources of threat feeds that are continually processed, prioritized, and mapped against Mitre Att&ck framework, our platform aims to serve as a one-stop hub for your cyber threat intelligence needs.
Key Features
Threat Intelligence Reports
Curated feed of threat reports to help you identify adversaries attacking sectors of your concern, with deep insight into the techniques, tactics and procedures (TTP’s) used
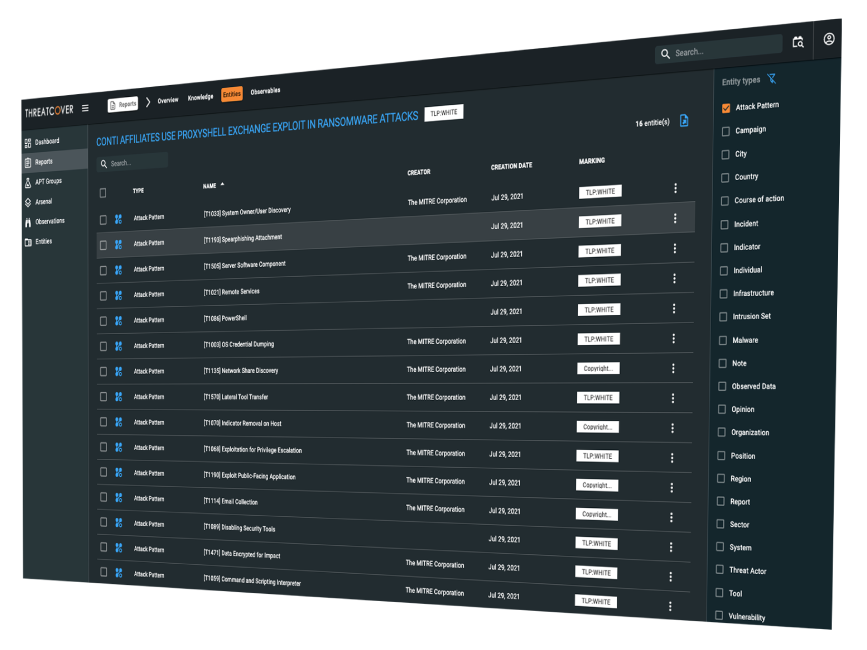
Centralized Threat Feeds
Contextualized and Normalized structured and unstructured threat data, available in various formats including STIX 2.1, XML, YARA, JSON, PDF, etc.
Track Global APT group
Gain comprehensive visibility into active APT groups, and get essential insights into the activities and TTP’s
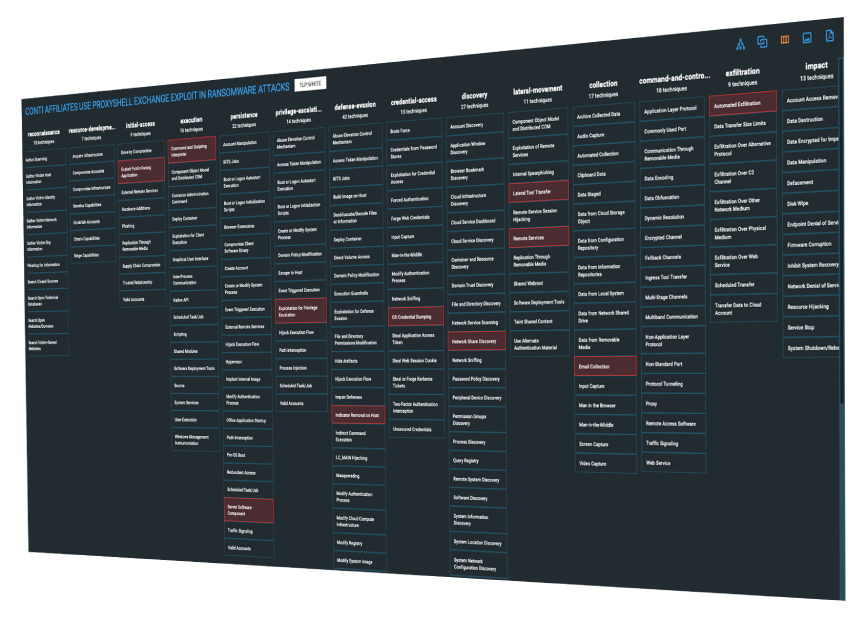
MITRE ATT&CK Integration
Automated mapping of threat data ingested into the platform to the MITRE ATT&CK framework
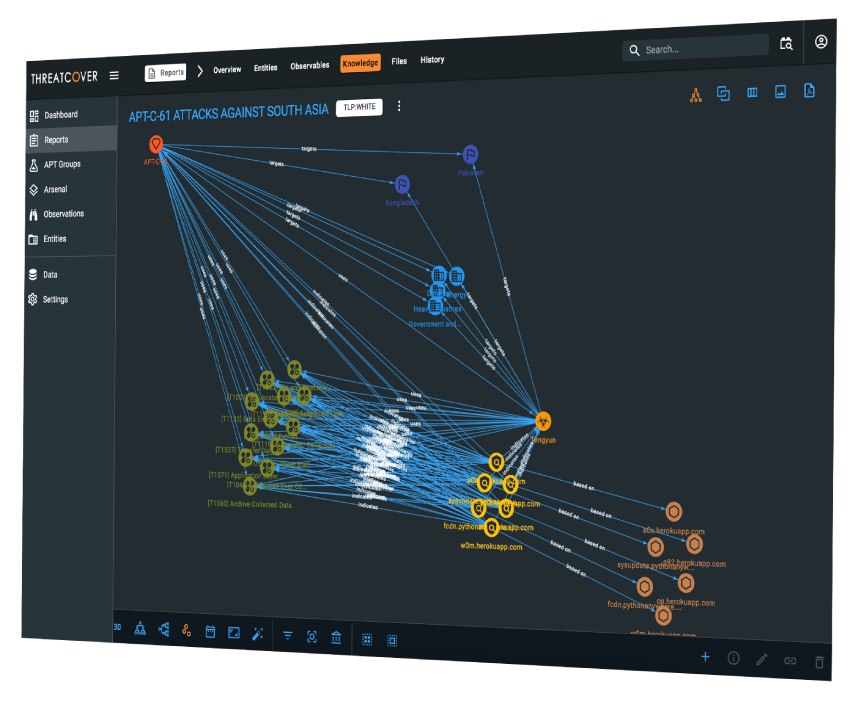
Rich Visualizations
Support of rich graph visualization to provide an interactive means to connect and explore complex cyber datasets.
API & Integrations
Export threat feeds in various formats to integrate with your security appliances and improve your cyber defenses
Solutions by