A systematic approach to understanding, identifying, and mitigating cyber threats
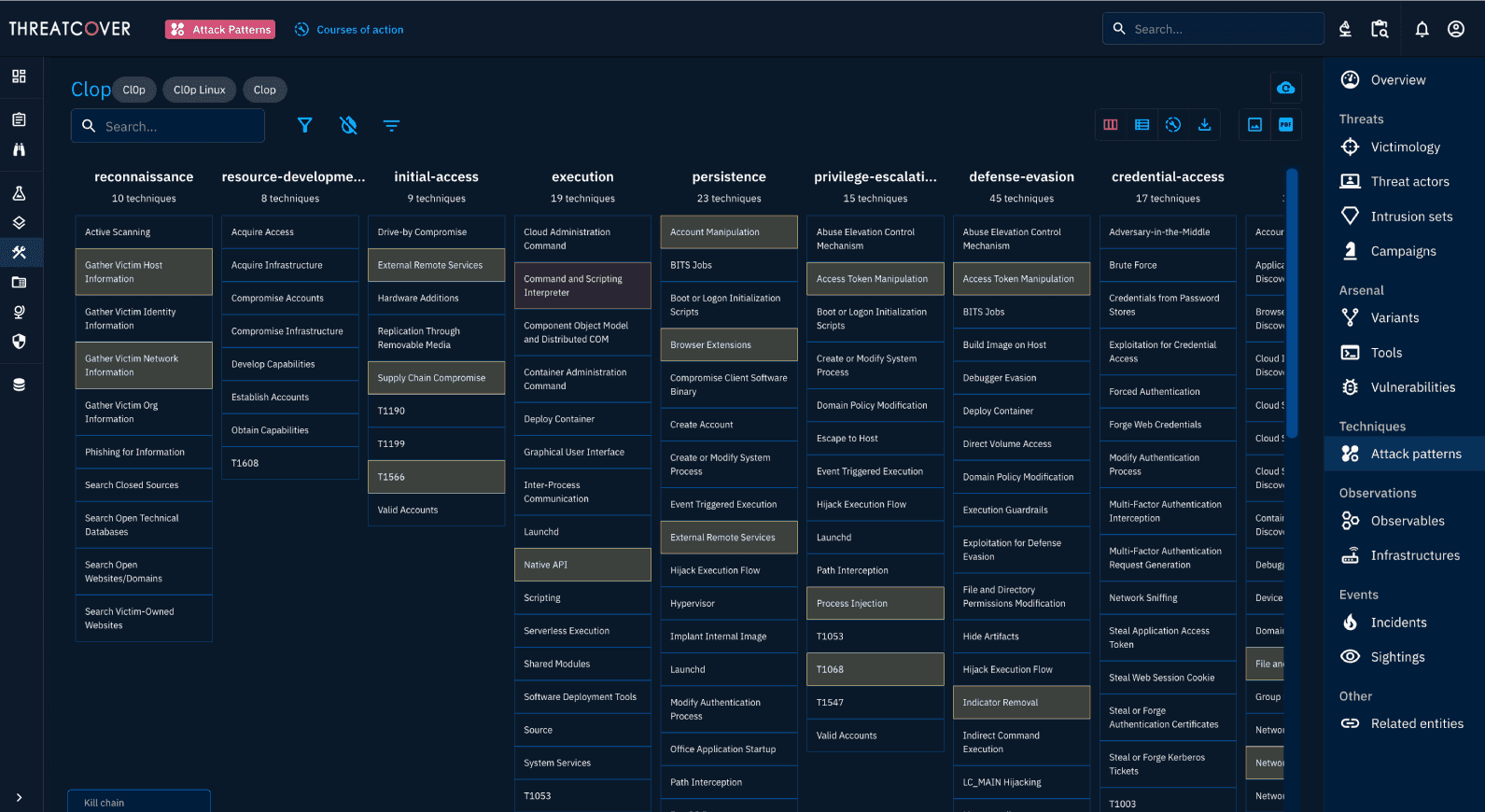
The Cyber Kill Chain mapping provides a comprehensive repository of malicious activities, enabling an extensive collection of actionable Cyber Threat Intelligence. By understanding the methodologies and goals behind cyberattacks, the inclusion of security controls is justified, thus offering hardening against all aspects of real-world cyberattacks.
Solutions by

Frequently Asked Questions
How does the Cyber Kill Chain help in understanding cyber threats?
The Cyber Kill Chain breaks down the stages of an attack, providing insights into attacker methods and behaviors.
What is the significance of actionable Cyber Threat Intelligence from Cyber Kill Chain mapping?
Actionable intelligence helps identify potential threats and develop targeted defense strategies.
How does the Cyber Kill Chain approach enhance security controls?
By understanding attack methodologies, organizations can justify and implement controls tailored to disrupt various stages of an attack.
Can organizations of different cybersecurity maturity levels benefit from the Cyber Kill Chain approach?
Yes, both mature and less mature organizations can use the Cyber Kill Chain to strengthen their security defenses.







