THREAT INTELLIGENCE SPECIFIC TO YOU
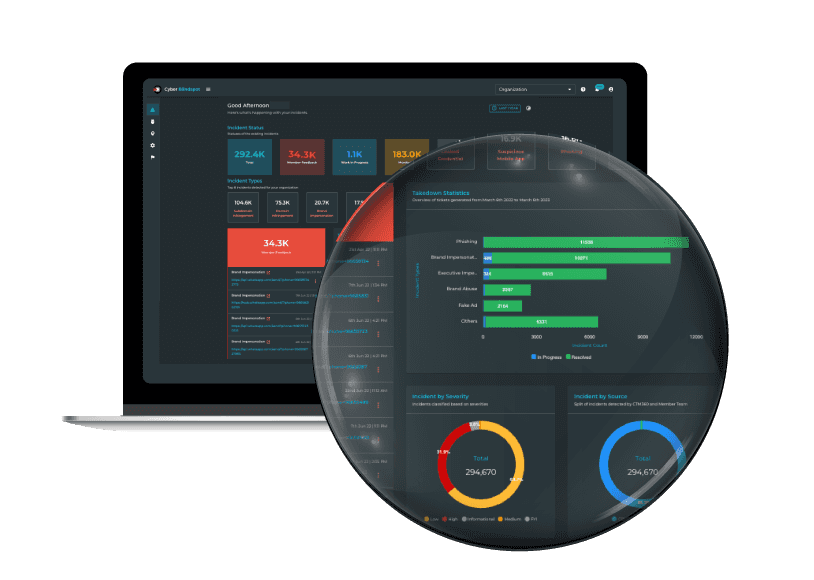
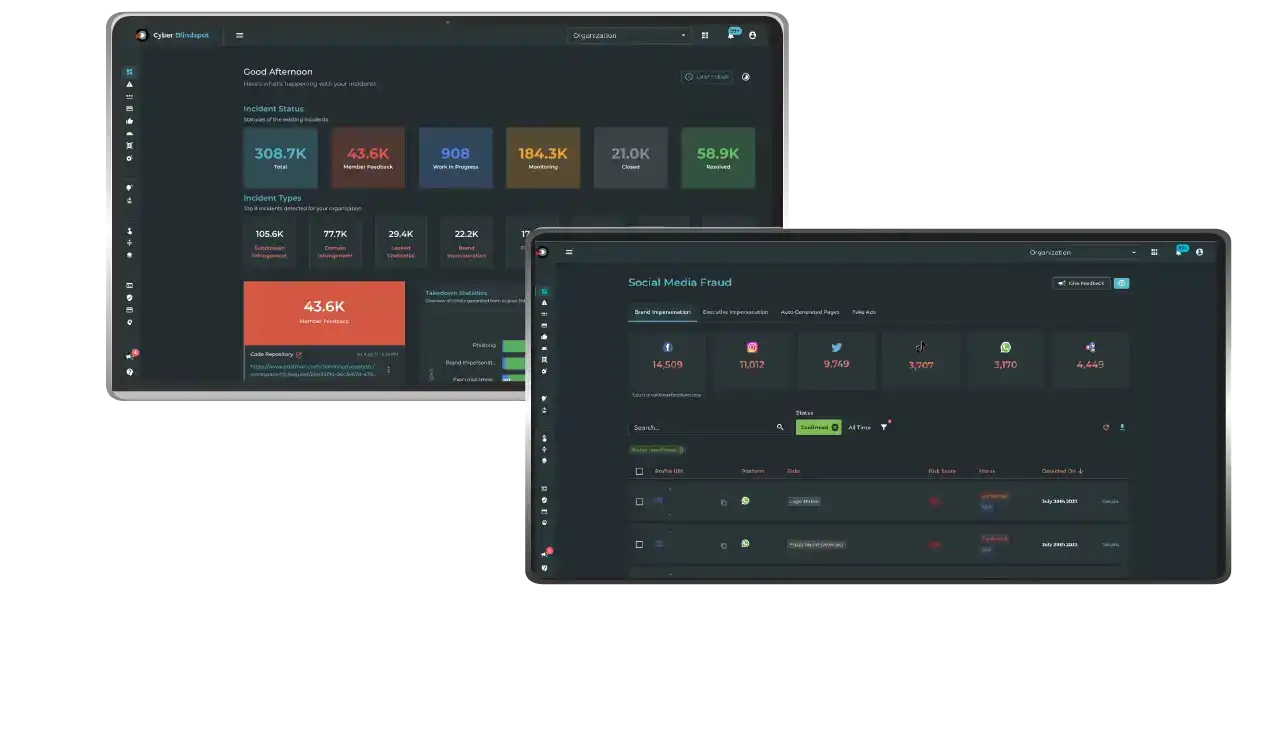
CyberBlindspot is CTM360's Digital Risk Protection platform which combines surface, deep, and dark web monitoring, including brand protection, anti-phishing, and takedowns. The platform enables you to take action on incidents derived from threat intelligence that is directly linked to your organization.
CyberBlindspot is noise-free, ensuring every incident identified is specific and relevant to your organization, brands and executives. The platform currently accounts for 50+ use cases, including phishing, impersonations, data leakage, rogue mobile apps, lookalike domains, credit card leakage monitoring, and all emerging threats.
We want to ensure that you have your security needs covered from all angles
Leverage global threat intelligence from the Surface, Deep & Dark web tagged to your assets so you know precisely what is targeting you.
Deep dive into Darknet monitoring and unravel your organization’s data.
Use this threat intelligence to view, manage and prioritize action on incidents.
Go beyond Indicators of Compromise using Indicators of Warning and Indicators of Attack so that your teams can manage threats before they impact you.
How It Works
Known and emergent threats are ever present often, making it overwhelming for your security teams.
The CyberBlindspot platform enables you to Capture, Curate, and Manage your threat intelligence feeds to ensure relevance and accuracy.
CAPTURE
- Open Source intelligence
- Tailored threat intelligence
- Infrastructure search engines
- News, blogs, paste sites, and hacker forums
CURATE
- Utilize in-house, open-source, and commercial enrichment systems
- Rule-based and heuristic-based pattern matching.
- A scoring mechanism for noise reduction.
MANAGE
- Triage and prioritize detected threats based on risk-level
- Manual and automated workflows to threats in a timely manner
- Feed result back into the system for rapid learning.
Solutions by