Attackers are exploiting SMS interfaces to send a large volume of One-Time Passwords (OTPs) or SMS messages to overwhelm the host servers, potentially denying access to legitimate services.
14 Feb 2023

We have received multiple reports regarding the growing threat of OTP/SMS flood attacks targeting businesses in the Kingdom of Saudi Arabia (KSA). Attackers are exploiting SMS interfaces to send a large volume of One-Time Passwords (OTPs) or SMS messages to overwhelm the host servers, potentially denying access to legitimate services.
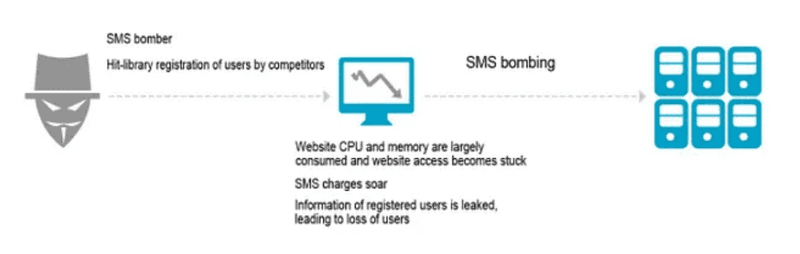
An OTP (One-Time Password) flood attack is a type of Denial-of-Service (DoS) attack that targets the corporate website's contact form, which often includes a field for users to enter their phone number or email address.
Here's how it works:
- The attacker uses automated software or a botnet to send a large volume of messages to the website's contact form, filling in the phone number field with a fake or random entry.
- The website's server receives a flood of incoming requests, each containing a fake or random phone number. The server attempts to process each request.
- The flood of incoming requests can overwhelm the website's server, causing it to slow down or crash, potentially leading to a denial of service for legitimate users.
In some cases, the flood of incoming requests can cause additional strain on the website's server, leading to increased data usage, additional charges, or other financial harm.
POSSIBLE IMPACT
SMS flood attacks can be disruptive and damaging for businesses, leading to loss of productivity, revenue, and reputation. It is important for businesses to have robust cybersecurity measures in place to prevent and mitigate the impact of such attacks. The possible impact may include but is not limited to:
- Poor website performance due to high CPU and memory usage
- Leakage of users’ data and loss of customers trust
- Account hacking and fraudulent transactions
- Disruption of business operations
RECOMMENDATIONS
To mitigate an OTP flood attack, there are a few key measures you can take:
Implement rate limiting: To prevent an attacker from overwhelming the system with a large number of OTP requests, you can implement rate limiting on the number of requests per user or IP address. This can help to prevent a single user from generating too many requests and causing a DoS.
Implement CAPTCHAs or other challenge-response mechanisms: To prevent automated bots from generating a large number of OTP requests, you can implement CAPTCHAs or other challenge-response mechanisms that require the user to pass a robot check.
Monitor system logs: Regularly monitoring system logs can help you detect and respond to suspicious activities, such as a large number of OTP requests from a single user or IP address.
Educate users: Providing users with information about OTP flood attacks and how to protect themselves can help to prevent successful attacks. This can include information on how to recognize suspicious requests and how to report them to the service provider. In many of these cases, a business may choose to leverage the use of an SMS/OTP gateway service to manage these operations.
- A gateway may have guards in place to account for many cases of abuse that can happen against these operations (sending, etc..). They allow to set of budget limits or limit the number of messages per second, minute, hour, or day.
- On the other hand, an application communicating with an SMS gateway should implement a few guards itself in case some restrictions are not applicable. Digital forms that precede requests heading for the SMS gateway should not allow for replay attacks as well as brute force attacks, by use of a CSRF token and/or CAPTCHAs.
- There should be ways to detect any such attempt of attacks as well as to mitigate any implications that may follow.
- When such attacks are detected, offending IP addresses should be blocked from communicating with the applications. The use of WAF appliances can also help reduce the chance of the risk of web application attacks.
- Use two-factor authentication: Two-factor authentication provides an additional layer of security and can help prevent unauthorized access to accounts.
By implementing the above measures, you can reduce the risk of an OTP flood attack and help protect your users and your business from the negative impact of such attacks.





